I thought I would write up a tutorial for tunneling HTTP over SSH as it is a great way to increase security and privacy of web surfing. I happen to work at a company that doesn't allow use of anonymous proxies (which is fine) but I don't necessarily want them viewing my web traffic either. Here is how I set up an HTTP tunnel to my home network from work.
My home setup consists of a Linksys WRT-54GL wireless access point connected to a high-bandwidth internet connection. The Linksys WRT-54GL is version 4 of the WRT-54G. With version 5 of the WRT-54G Linksys changed the hardware and stopped using Linux internally. Because of these changes the device could no longer run third-party firmwares. The WRT-54GL is Linksys' response to hobbyists (hackers) who still want to tinker with other firmwares. For this tutorial you'll need a router capable of running the DD-WRT firmware. This excellent firmware has many great features including an SSH daemon which is a prerequisite for our tunneling. A list of supported devices can be found here.
Instructions for flashing the firmware can be found all over the Internet. I'll assume the reader can flash the router and get the DD-WRT firmware running (Administration->Firmware Upload). Some Linksys routers (including the WRT-54GL) have a 3MB limit to firmware size so if that is the case use the mini version of DD-WRT first, once that is running upload the version you want.
I'm using DynDNS to keep tabs on my dynamic Internet IP address. This free service allows you to keep your changing IP address up to date and matched to a hostname. DD-WRT has support for automatically keeping the address updated. Other services are supported too so you can choose your favorite. Once your dynamic DNS account is created you can enter the relevant information into the Setup->DDNS tab in DD-WRT.
The next thing you will need to do is enable the SSH daemon. This can be done throughout the Administration->Services tab in DD-WRT. Under SSHD select enable. The login will be username:root password:[your router password].
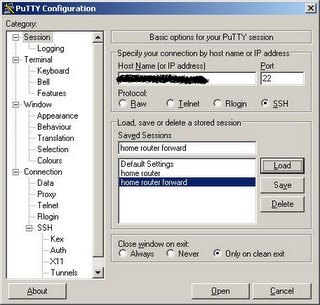
To connect to the SSH server and tunnel HTTP you will need the Putty SSH client. To connect to your router enter the hostname or IP address of your router on the Session tab:
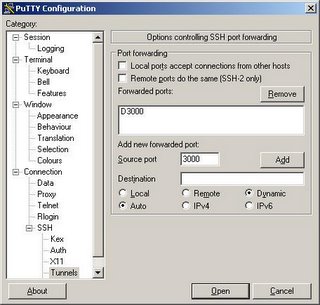
Next, to setup the tunnel click on Tunnels, enter 3000 (or whatever local port you'd like to use) for the source port, click Dynamic and click Add. This will create a SOCKS proxy on your local machine on port 3000 (or whatever port your chose) that you can use with your web browser.
Now you can click Open to log into your router. The tunnel isn't created until you log in. Remember that your username is root and your password is your router password (you changed it right?).
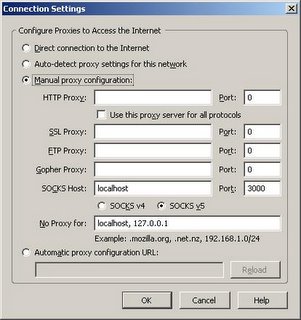
Now you're ready to connect your web browser. Using Firefox, you will have to configure a proxy server. Click Tools->Options. Then under General click Connection Settings. On this screen you can configure the SOCKS proxy that you've set up using Putty. Select Manual proxy configuration, enter localhost for the SOCKS host and 3000 for the port (or whatever you used). Click OK. You should now be tunneling through your home router over ssh.
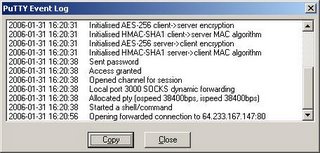
You can verify that the connections are being forwarded by looking at the Putty Event Log. You should see something similar to the following after loading www.google.com in your web browser.
My home setup consists of a Linksys WRT-54GL wireless access point connected to a high-bandwidth internet connection. The Linksys WRT-54GL is version 4 of the WRT-54G. With version 5 of the WRT-54G Linksys changed the hardware and stopped using Linux internally. Because of these changes the device could no longer run third-party firmwares. The WRT-54GL is Linksys' response to hobbyists (hackers) who still want to tinker with other firmwares. For this tutorial you'll need a router capable of running the DD-WRT firmware. This excellent firmware has many great features including an SSH daemon which is a prerequisite for our tunneling. A list of supported devices can be found here.
Instructions for flashing the firmware can be found all over the Internet. I'll assume the reader can flash the router and get the DD-WRT firmware running (Administration->Firmware Upload). Some Linksys routers (including the WRT-54GL) have a 3MB limit to firmware size so if that is the case use the mini version of DD-WRT first, once that is running upload the version you want.
I'm using DynDNS to keep tabs on my dynamic Internet IP address. This free service allows you to keep your changing IP address up to date and matched to a hostname. DD-WRT has support for automatically keeping the address updated. Other services are supported too so you can choose your favorite. Once your dynamic DNS account is created you can enter the relevant information into the Setup->DDNS tab in DD-WRT.
The next thing you will need to do is enable the SSH daemon. This can be done throughout the Administration->Services tab in DD-WRT. Under SSHD select enable. The login will be username:root password:[your router password].
To connect to the SSH server and tunnel HTTP you will need the Putty SSH client. To connect to your router enter the hostname or IP address of your router on the Session tab:

Next, to setup the tunnel click on Tunnels, enter 3000 (or whatever local port you'd like to use) for the source port, click Dynamic and click Add. This will create a SOCKS proxy on your local machine on port 3000 (or whatever port your chose) that you can use with your web browser.

Now you can click Open to log into your router. The tunnel isn't created until you log in. Remember that your username is root and your password is your router password (you changed it right?).
Now you're ready to connect your web browser. Using Firefox, you will have to configure a proxy server. Click Tools->Options. Then under General click Connection Settings. On this screen you can configure the SOCKS proxy that you've set up using Putty. Select Manual proxy configuration, enter localhost for the SOCKS host and 3000 for the port (or whatever you used). Click OK. You should now be tunneling through your home router over ssh.

You can verify that the connections are being forwarded by looking at the Putty Event Log. You should see something similar to the following after loading www.google.com in your web browser.

No comments:
Post a Comment