For the security minded, one of the scariest revelations from the now three-year-old Snowden leakshad nothing to do with accommodating ISPs (shocking) or overreaching and often vague anti-terrorism practices and policy (an even bigger shock, right?). Instead, when news trickled out about matters like the National Security Agency’s Vulcan data repository or its Diffie-Hellman strategy, online privacy advocates found themselves quaking. Suddenly, seemingly everyone had to re-evaluate one of the most often used tools for maintaining a shred of anonymity online—the VPN.
VPNs, or virtual private networks, are typically used to obfuscate users’ IP addresses and to add a layer of security to Web browsing. They work by routing traffic through a secure, encrypted connection to the VPN’s server. The reasons for using VPNs vary. Some people use VPNs to change their IP address so they can access location-specific media content in a different geographic location or download things on torrent that are less likely to be traced back to them. Others hope to minimize online tracking from advertisers, prevent the negative effects of rogue access to Wi-Fi networks, or even just obfuscate their IP address to specific sites they visit.
Not all VPNs are alike, however. In fact, poorly configured VPNs can make users more vulnerable in various ways. Some ban torrenting altogether. Others log information, either for maintenance reasons, to track abuse, or in accordance with their local data retention laws.
Last year, I set out to put together a list of the best current VPNs for Ars. Although there are multiple “top VPN” lists available online, they are often riddled with affiliate links, making it hard to ascertain their accuracy. An independent online VPN comparison chart outlines VPN business practices, logging, service configuration, and other features, pinpointing contradictory policies and misleading claims that various services are 100 percent effective. But much of the information is still likely compiled from the actual VPN websites, meaning some misleading marketing claims could sneak in.
Several months of research later, I have failed. Today, I still can’t make good faith recommendations for VPNs that guarantee the safety and security of interested users. Instead, the reporting process has only complicated my view of modern VPNs. Evaluating what works and what doesn’t isn’t always straightforward, and verifying the accuracy of this stuff isn’t easy either (especially when it comes to logging). So rather than a simple list of services to use, all I can offer are a handful of guidelines to keep in mind when determining if a VPN can be effective for you in 2016.
VPNs are not for anonymity
One common misconception about VPNs is that they provide user anonymity—even in the face of nation-state actors. “If the objective is to limit exposure to mass surveillance from governments, a VPN is likely not adequate,” said security researcher Kenneth White. In fact, VPNs claiming to offer users anonymity are “inept, irresponsible, or both,” Jeremy Campbell, creator of DNSleaktest.com, told Ars in an e-mail. “Using public VPNs for anonymity is foolish and potentially dangerous, no matter how securely it’s configured, simply because the technology was not designed at all for anonymity. VPN services require that you trust them, which is a property that anonymity systems do not have.”
White didn’t insist on abandoning VPNs altogether at this point, but he cautioned that they should be thought of as a single, supplemental tool and not as a privacy solution. “Instead, the use of strong privacy tools such as the Tor Browser (possibly coupled with a reputable VPN) is a must,” he said. “Not only because of the anonymizing properties, but because the bundled browser has been heavily modified to maximize Web privacy (via cookies, Flash, and Java plugins).”
Tor has a distributed network that attempts to preserve anonymity by running traffic through multiple relays. But this is also hard to verify, and nobody knows for certain whether or not Tor can be reliably successful. The browser’s recent high-profile encounter with the US Department of Defense only heightens such caution. And some critics in fact argue that Tor makes people more susceptible due to its reliance on an outdated version of Firefox. The takeaway? Tor and even the Tor Browser are not entirely foolproof, either.
“There have been some malicious Tor exit nodes in Russia that have actually been modifying binaries, so if you download a piece of software through Tor and you happen to be unlucky enough to get one of these Tor exit nodes, they’ll actually modify it so it becomes malware,” said Matthew Green, a cryptography professor at Johns Hopkins University.
Although Green has never heard of that happening with a VPN, he pointed out the same attacks are possible. In contrast to most VPNs, however, Tor and the Tor Browser are used in incredibly high-risk situations, meaning engineers work incredibly quickly to patch security vulnerabilities. The same may not be true for all VPNs.
VPNs are not necessarily safe for torrenting
Some VPN providers do not permit peer-to-peer sharing and would even turn over user names to a copyright holder if necessary. Others issue warnings on behalf of the copyright holders and may cancel the accounts of repeat offenders. Anyone wishing to use a VPN for private torrenting and streaming can look for a provider that doesn’t disclose information when served with a DMCA notice (or one that doesn’t retain logs), though the same issue comes up again.
“However, there’s no way for users to verify what VPN providers say,” Campbell said. “They must judge providers by reputation, relying on news reports, discussion in online forums, and so on.”
VPNs do not offer robust protection from ad tracking
Although VPNs mask your IP address, they won’t necessarily protect you from spying ads and invisible trackers. “VPNs alone provide negligible protection against ad network tracking, because an IP address (which the VPN is masking) is a weak identifier,” Campbell said. “Ad networks prefer browser cookies, supercookies, and browser fingerprinting techniques ( https://panopticlick.eff.org) that VPNs cannot protect against.”
To protect against ubiquitous ad tracking, ad blockers (like uBlock or uBlock origin) and tracking blockers (like PrivacyBadger or Disconnect) provide some level of protection. Disabling JavaScript or using tools like NoScript for Firefox can offer some protection from fingerprinting. Advanced users can use virtual machines or multiple browsers isolated in sandboxes. Using the Tor Browser can protect against browser fingerprinting as well.
VPNs could put you at risk
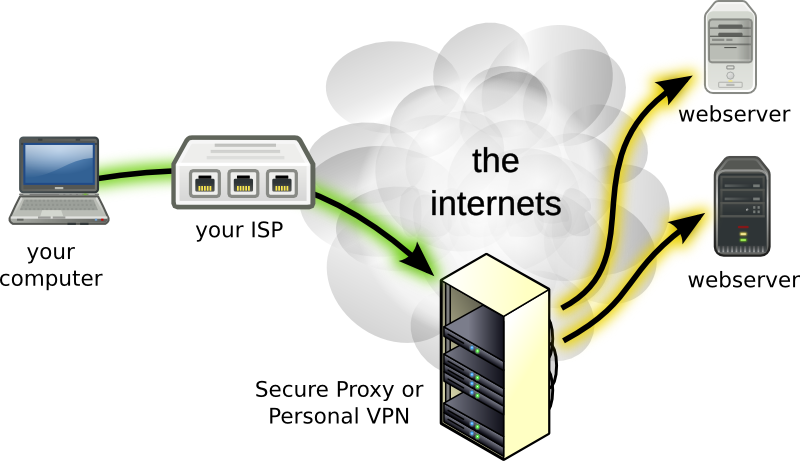
The best use case for consumer VPNs is local network security, especially on public Wi-Fi networks in airports, hotels, cafes, and even on airplanes (especially since GoGo has been caught issuing fake HTTP certificates for YouTube, which could expose all user traffic—including users’ YouTube passwords—to the inflight broadband provider).
Since VPNs create a tunnel between a user and the VPN provider’s server, though, it’s again important to have trust in the VPN provider. That provider can essentially see all of your traffic, log all of your traffic, and even modify your traffic. An improperly configured VPN could potentially give others direct access to your private local LAN, which is likely significantly more dangerous than shady people sniffing your traffic at the coffee shop.
“You’re really putting yourself at their mercy if they’re not honest,” said White. “Your fear may be that you’re going to get hacked by someone on the local network, but [by using a sketchy VPN] you’re basically putting yourself in the hands of your worst possible attacker. All of your traffic is going through the worst coffee shop access point in the world if you pick the wrong VPN service.”
Preshared keys
White offered a quick list of VPNs that have preshared keys posted online: GoldenFrog, GFwVPN, VPNReactor, UnblockVPN, IBVPN, Astril, PureVPN, PrivateInternetAccess, TorGuard, IPVanish, NordicVPN, and EarthVPN.
“If I know the preshared key for your VPN and I am somebody who has control of the Wi-Fi access point, and you’re using a preshared key with a VPN I know, then I can basically man-in-the-middle attack and decrypt everything you’re doing,” said White. “The security you get against that kind of attacker when the preshared key is known is not very strong.”
PPTP instead of IPSec, L2TP/IPSec, IKEV2, or OpenVPN
Some VPNs use the outdated PPTP VPN protocol, which is fundamentally insecure. Better options include IPSec (LibreSwan and StrongSwan, which are actively maintained), L2TP/IPSec, IKEv2, or OpenVPN.
Among these alternatives, IPsec can be set up without installing extra software, but some believe it was either compromised or intentionally weakened by the NSA. OpenVPN is more secure but can be more difficult to set up and requires third-party software. It also needs to be configured correctly.
Recent research by High-Tech Bridge found that 90 percent of SSL VPNs tested use insecure or outdated encryption. In total, 77 percent used the insecure SSLv3 (or even SSLv2) protocols, 76 percent used an untrusted SSL certificate (making it easier for remote attackers to perform man-in-the-middle attacks and intercept all data passing over the VPN connection), and a large chunk used insecure key lengths for RSA signatures, insecure SHA-1 signature. Believe it or not, 10 percent were still vulnerable to Heartbleed.
Data retention/logging
Some VPNs log information to be in compliance with data retention laws in their respective countries. And a lot of VPNs overall log information, such as when specific users connected, where they connected from, and even what connections they made. It’s not entirely easy to know whether to trust VPN claims that they do not log.
Even VPN providers that log less than others often do log usage data (including incoming connections, either by IP address or user name) and internal routing on the network they use for internal load balancing or server maintenance. This creates a record of user accounts or connections and outgoing IP addresses—which is quite a bit of information. Some logs are only held in volatile memory, but others are not, often due to retention laws in various countries. Ultimately, the information kept can be enough to de-anonymize VPN users if combined with usage data from that person’s computer or connection logs from another site.
Reading the terms of service closely may help you determine whether logs are maintained, what is retained, for how long it's retained, and perhaps even how such information would be used in which instance—but again, the claims are hard to verify. Folks thinking that VPNs will protect user identities in the case of criminal activity will be disappointed to learn that the US government actually has mutual legal assistance treaties with dozens of countries throughout the world.
Leakage
"From a technical point of view, I think the most underrated vulnerabilities are network leaks in the client-side VPN software,” said Campbell. Even after a user has connected to a VPN server, a few outgoing packets may not be using the VPN tunnel, which could compromise their privacy. “That could be life threatening. VPNs have been rightly criticized about this vulnerability by many in the security/anonymity community (e.g., https://www.usenix.org/system/files/conference/foci12/foci12-final8.pdf).”
Some VPNs do have settings that block insecure communications before they have a chance to activate, such as when you first sign onto a Wi-Fi hotspot or switch from one to another. Other providers allow users to set up firewall rules.
In June 2015, a group of researchers from Sapienza University in Rome and Queen Mary University in London tested 14 popular commercial VPN services and found that 10 of them leaked IP data, and all but one were vulnerable to IPv6 DNS hijacking attacks. The researchers did not comprehensively recheck VPNs to see if they deployed fixes, but they did run some ad hoc tests and found improvement. Again, though, it’s not easy to determine which VPNs that say they fixed this and other issues actually have.
“The advice that I would give people is that, if you’re worried about government monitoring, you should always use Tor, full stop,” said Dr. Gareth Tyson, a lecturer based at Queen Mary University of London and one of the authors of the study.
Again, this could prove to be an imperfect solution. While the Tor Browser may offer anonymity, censorship circumvention, and protection from monitoring and tracking, it’s not as speedy as using a VPN. Some ISPs unfortunately block Tor relays to boot.
Marketing hype
Hopefully, Ars readers can identify a majority of the online snake oil that exists. VPNs aren’t exempt, and many make claims that lack credibility (offering “100 percent online security,” for example).
“Take a really skeptical look at a service provider that makes claims of no logging, accepts Bitcoin, and makes any kind of grandiose claims about military grade or government-proof or NSA-proof encryption,” said White. Not only could VPNs have lax security, some may be honeypots run by nation-state actors. Conversely, VPNs that are very clear about their threat model and what they can and cannot protect against are likely more trustworthy.
Reading terms of service can sometimes provide a bit more clarity. For example, in 2015, the free version of the Israeli-based VPN Hola was caught selling users’ bandwidth to Luminati VPN network, and users who cloaked their IP addresses unwittingly became VPN exit nodes or endpoints (exposing their own IP address and associating it with other people’s traffic). Hola did not update its FAQ for clarity until 8chan message board operator Fredrick Brennan stated that Hola users’ computers were unwittingly used to attack his site.
What to look for
Given all the precautions and VPN footnotes above, is it feasible to find workable VPNs or at least reliable information about them? “Assertions from VPN service providers are absolutely caveat emptor, in the absence of public third-party audits,” White pointed out. “You’re getting Pinky-Promise-as-a-Service.”
That said, there are many positive signs to look for when evaluating a VPN beyond the basics: is the VPN using up-to-date protocols, what’s the reputation of the company and the people behind it (and their history or expertise), are terms of service easy to understand, what does the VPN protect against and what doesn’t it cover, and is the service honest about its disclosures?
Aside from these factors, Campbell recommends looking at any company activism, which he says is likely to demonstrate how much an organization cares about customer privacy. He also looks for a clear and unambiguous privacy policy rather than a boilerplate policy and for companies that have been in business for at least three years.
“There has been an explosion of cheap VPN providers over the last few years since the Snowden revelations,” Campbell warned. “Many of these new providers use laughable security practices. In many cases, they are Web hosting businesses that have decided to repurpose some of their servers, effectively becoming bandwidth resellers, but with no security experience.”
As a final precaution, Campbell also looks for VPNs that do not use third-party systems to capture sensitive customer data. “Any VPN service that respects their customers’ privacy will self-host all systems that interact with customers, such as third-party live chat scripts, support ticketing systems, blog comments, etc. Customers often submit very sensitive information in support requests without knowing that the VPN provider doesn't have exclusive control over the system,” he said.
DIY
Depending on your privacy needs, a pre-made solution may not currently exist. If that’s the case, technical users can roll their own VPNs. If a pre-made solution is more your speed, one option isrunning Streisand over a DigitalOcean VPS, Amazon Web Services, Vultur, OVH, or another reputable hosting provider. Created in the aftermath of Turkey blocking Twitter, Streisand's goal is to help users circumvent Internet restrictions.
“Streisand sets up a new server running L2TP/IPsec, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, and a Tor bridge. It also generates custom configuration instructions for all of these services,” the GitHub page reads.
Creator Joshua Lund told Ars that one of Streisand’s goals is to make the setup process as painless as possible. He envisions the open-source service growing into a ”centralized knowledge repository” where the best practices can be updated and automated by a watchful community.
“Streisand automates several difficult steps that can dramatically increase security,” Lund told Ars in an e-mail. “For example, Streisand's OpenVPN configuration enables TLS authentication (AKA an ‘HMAC firewall’), generates a custom set of Diffie-Hellman parameters, and enables a much stronger cipher and checksum algorithm (AES-256/SHA-256 instead of OpenVPN's antiquated default of Blowfish/SHA1). Many users will skip these optional and time-consuming enhancement steps if they are configuring OpenVPN by hand. In fact, most commercial VPN providers don't enable these features in their OpenVPN setup.”
Other benefits of Streisand include automatic security updates and an automated setup process that allows users to get a brand new server running in around 10 minutes. And when compared to commercial VPN providers, Streisand-deployed servers are far less likely to become targets of censorship efforts, DDoS attacks, or blocked access to streaming services.
Like VPNs at large, your mileage with Streisand may vary. And after surveying the state of such offerings in 2016, there may only be one truly universal rule: What to look for in a VPN depends on what you’re using it for in the first place. A user looking for local network security has different needs than someone using a VPN for geoshifting, for example, so these decisions can get complicated fast. But being aware of the limitations of VPNs in general and knowing what specific weaknesses and pitfalls to avoid can at least help you make a more informed complicated decision.
from
http://arstechnica.com/security/2016/06/aiming-for-anonymity-ars-assesses-the-state-of-vpns-in-2016/ ,
http://arstechnica.com/security/2016/06/aiming-for-anonymity-ars-assesses-the-state-of-vpns-in-2016/2/
相关帖子:
Streisand-寻找完美的 VPN
-------------------------------------------------------
翻墙?隐私?今天聊聊VPN的那些事
三年前斯诺登泄密事件揭露的东西,从安全的角度看对互联网服务提供商来讲并没有太多的帮助,甚至可以说做的有些过火。同时也模糊了反恐政策的概念。而当新闻爆出像NSA的Vulcan数据库或者它的Diffie-Hellman策略时,任何一个网络隐私主义者看过了都会心中发颤。突然间似乎每个人都需要重新评估下某些网上用于保持隐私的工具——VPN。
传统VPN简介
VPN(虚拟专用网络),这款工具通常用于混淆用户的IP地址,或在用户进行WEB浏览时增加一层安全保护。它会把你的流量转到加密且安全的VPN服务器上。不同的人使用VPN的目的也不同,有些人可能是用它来改变自身的IP地址,这样就可以获取一些其他地域的媒体内容,或者能匿名下载一些东西。还有的人希望以此规避广告商的网络追踪,或者防止盗用WIFI后的负面影响,甚至只是为了在他们访问特定网站时隐藏真实的IP地址。
然而VPN的质量也是参差不齐的。事实上某些存在问题的VPN会让用户的安全更加脆弱。某些VPN是禁用了torrent下载的,还有些会记录下信息,跟踪上网行为,或者按照当地的法律对数据进行保留。
去年我开始尝试整理一份好的VPN列表,虽然网上已有不少类似的VPN清单,但是通常都充斥着附加内容链接,很难确认其准确性。这份VPN比较图表,里面概述了VPN业务流程、日志记录、服务配置和其他特性。但它存在矛盾策略,并误导读者,声明各类的服务是100%有效的。但其实大部分内容是从真实的VPN网站导入的,这就意味着可能会混入一些错误信息。
几个月的研究后,笔者的尝试都失败了。所以现在笔者仍然不能推荐一组安全的VPN列表给大家。相反的是,研究结果刷新了笔者对目前VPN的三观。当涉及到日志记录的时候,评估可行性和验证准确性也不是件容易的事,所以,我觉得与其给大家一个简单的列表,还是提供一些指导方针更加靠谱,让大家自己了解在本年度哪些VPN是有效可用的。
VPN不是用来匿名的
关于VPN的一个常见的误读是:它们会给大家提供匿名功能,即使是针对民族主义者。但是,安全研究员Kenneth White表示:
“如果政府对目标进行专门的监测追踪,VPN是不足以做到这一点的。”
事实上,VPN声称的会给提供用户匿名性,是“不可行的,不负责的,或者两者兼备的”。DNSleaktest.com的站长Jeremy Campbell在邮件里告诉记者:
“为了实现匿名去使用公共VPN是非常愚蠢而危险的,无论服务配置的有多么安全,匿名技术本身并没有在这里实现。VPN服务要求你信任他们,但匿名系统本身是没有这个属性的。”
White没有坚持完全放弃VPN,但是他警告说它应该作为一个辅助工具,而不是一个隐私的解决方案,他表示:
“相反,像专门的隐私工具如Tor浏览器之类的(里面可能包含了信用良好的VPN),那就是可以使用的。它们不仅实现了匿名化属性,而且浏览器已经进行了大量定制,以实现网络隐私的最大化(比如弱化了cookie、Flash、Java插件等特征)。”
Tor分布式网络,会尝试在多个中继传输流量来实现匿名。但其实它也很难进行核实,没有人知道Tor这样是否能够获得百分百成功。Tor浏览器最近受到了美国国防部的瞩目,这只会强化这种担心。某些批评者认为,Tor会让人们更容易依赖过时版本的Firefox,但这些东西都不能保证是万无一失的。
Johns Hopkins大学的密码学教授Matthew Green表示:
“某些在俄罗斯出口节点的恶意Tor,实际上会偷偷修改二进制文件。所以,如果你不幸在Tor下载文件时碰巧遇到了这些节点,它们可能会将它转换成恶意软件。”
尽管Green并没有听说过VPN发生过这样的事,但他指出这样的攻击是存在可能的。与多数VPN不同,Tor和Tor浏览器通常用于高风险的情况,工程师需要迅速修复安全漏洞,这样的方式可能不适用于所有的VPN。
用VPN来BT下载安全吗?
某些VPN提供商会禁用p2p,如果有必要还会把用户的名字给版权所有者。代表版权所有者的利益的,可能会取消惯犯的账户。希望使用VPN进行torrent下载和流媒体观看的亲们,可以寻找那些特殊的服务提供商(或者不保留日志),但是问题又来了,Campbell表示:
“然而,我们并没有办法验证VPN提供商所说的话。大家必须依靠新闻报道和网上论坛的讨论等等,来判断服务提供商的声誉。”
看来,必须时刻保持警惕才行。
VPN可以“防御”广告追踪?
尽管VPN能掩饰你的IP地址,但它不一定能保证你免受间谍广告和追踪的困扰。
Campbell表示:
“VPN提供的防广告追踪的技术可以忽略不计,因为IP掩盖是一个弱标志。网络广告更倾向于cookies、supercookies和浏览器指纹技术,这些东西VPN是无法进行保护的。”
为了防止无处不在的广告跟踪,广告阻断器uBlock、uBlock origin,以及追踪阻断器PrivacyBadger或Disconnect会提供一定程度的保护。禁用JS代码,或者使用Firefox下的NoScript可以消除一些指纹。更高级的用户可以使用虚拟机或者沙箱浏览器。当然,Tor浏览器也能防止产生特定浏览器指纹。
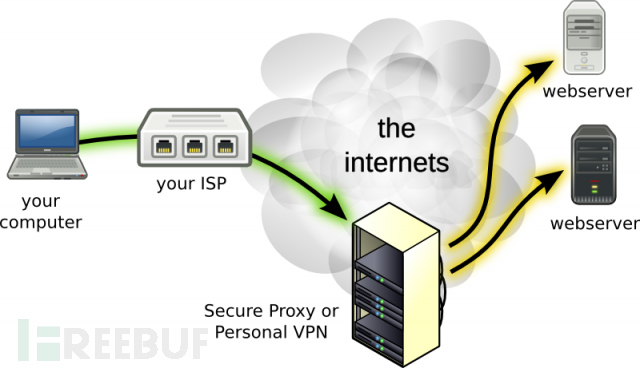
VPN让你更危险?
用户使用VPN的是为了保护自身网络安全,特别是在处于公共WIFI之下的时候。GoGo被爆出使用了Youtube的伪造证书,这可能会泄露用户的流量,包括用户的Youtube密码。
因为VPN建立了用户和VPN商服务器之间的通道,所以用户对于VPN提供商的信任非常重要。毕竟提供商能看到和记录你所有的流量,甚至可以更改你的流量内容。一个VPN的配置不当,黑客就可能直接访问你的本地局域网,这比别人在咖啡店网络下,嗅探你的流量更加可怕。
“如果VPN服务供应商不老实的话,你只能自己做祈祷了。你得时刻担心是否会在本地局域网被人黑掉,若是使用了一个粗制滥造的VPN服务,很可能就会把自己推入虎口。”
预共享密钥
White提供了一个VPN的列表,在网上已有共享密钥发布:
GoldenFrog、GFwVPN、VPNReactor、UnblockVPN、IBVPN、Astril、PureVPN、PrivateInternetAccess、TorGuard、IPVanish、NordicVPN、EarthVPN。“如果我知道了你正在使用的VPN预共享密钥,并且我控制了你所在WIFI的热点,那么就可以进行中间人攻击并且解密你的上网行为。也就是说,当黑客拥有这预共享密钥时,您的网络安全系数就降低了。”
PPTP的代替品
一些VPN还使用了老掉牙的的PPTP VPN协议,这在根本上就是不安全的。更好的选择包括IPSec(有人积极维护)、L2TP/IPSec、IKEv2以及OpenVPN等等。
在上述的几个选项中,IPSec可以设置为不需要安装额外的软件,但有人认为这是故意破坏和削弱NSA(美国国家安全局)的力量。OpenVPN比它还要安全,但是搭建手法更加复杂,需要第三方软件的帮助,以及用户进行正确且复杂的配置。
根据High-Tech Bridge最近的研究发现,SSL VPN中,有90%会使用不安全的或者过时的加密。而有77%使用了不安全的SSLv3(甚至SSLv2)协议,76%用了不可信的SSL证书(黑客可以更轻易的进行中间人攻击,拦截VPN连接中的流量),更有一大部分用的不安全的RSA密钥长度的签名,以及不安全的SHA-1签名。不管你信不信,其中还有10%存在心脏出血漏洞。
数据保留和日志记录
一些VPN会根据本国或当地的法律,进行日志信息保存。而且许多VPN服务提供商会记录大量信息,比如在特定的用户来连接时,是从哪里、从什么时候连上的,甚至还有他们做了哪些连接。
甚至有些VPN服务提供商,日志量少时会记录下重要日志,比如连接的IP地址和用户名,以及内部路由使用的内部负载均衡和服务器维护。某些VPN服务提供商的日志记录可能会很快销毁,而其他的由于本地的相关法律,处理方式会有所不同。不管怎样日志里保存的信息都是足以破除用户匿名性的。
仔细阅读服务条款会帮助你确定服务商日志维护保留的情况,并可以了解他们会如何使用收集到的信息。但是其中的真伪也很难验证。有人认为进行犯罪活动时VPN也会保护用户的身份,但人家美国政府已经与世界上数十个国家签署了司法互助条约了。
泄露用户隐私
即使用户已经连上了VPN服务器,但某些发出的包可能没有经过VPN通道进行通信,这就泄露了用户的隐私。
Campbell表示:
“从技术角度来讲,我认为最被低估的漏洞就是VPN软件客户端的网络信息泄露。严重的时候,它可能会危及用户的生命,许多网络安全和隐私社区已经对此漏洞进行了重点关注。”
一些VPN服务提供商设置了规则,在用户出篓子之前,能阻止不安全的连接。比如你首次登入某个WIFI热点,或者从一个热点转入另一个的时候。其他服务商还会允许用户自己设置防火墙规则。
2015年6月,罗马Sapienza大学和伦敦玛丽女王大学的研究人员测试了14款热门的商业VPN服务,他们发现了其中10个会泄露IP的数据,且都会遭受IPV6 DNS劫持攻击。虽然后期研究人员并没有全面复查他们是否修复了,但是也做了一些特别的测试,并发现情况有所改善。但是可能修复了问题后,还存在其他漏洞。
伦敦玛丽女王大学的研究员GarethTyson博士表示:
“我给大家的建议是,如果你担心被政府监控,你应该全方面使用Tor。”
同样,这可能也是一个不完美的解决方案。虽然Tor浏览器提供匿名、规避审查和反监控追踪,但是它并不像VPN一样迅速。更糟糕的是,某些互联网服务提供商会拒绝Tor。
营销宣传
许多声称安全的VPN服务提供商,其实缺乏可信度。某些VPN服务提供商声明不会记录日志,接受比特币,浮夸地表示他们是军用、政府、NSA级别的加密。
而且,VPN不仅仅会存在安全漏洞的问题,还可能是民族主义者的蜜罐,相反,那些事先声明他们的威胁模型,讲清楚能保护的和不能提供保护VPN服务提供商,可能更值得信任。
阅读服务条款有时能给用户一个清晰的认识。比如2015年,免费的以色列VPN Hola被发现将用户带宽出售给Luminati VPN。那些想要隐藏IP地址的用户不知不觉就变成了VPN的出口节点和终点(暴露了自己的IP地址,混入了别人的流量)。直到8chan留言板运营商 Fredrick Brennan说,直到Hola用户在不知不觉中被利用来攻击他的网站后,才更新了自己的FAQ。
如何寻找可信的VPN
看到上面所有的预防措施和VPN说明了吧,靠它们去找可信的VPN靠谱么?VPN服务提供商表示购者自慎。
某家VPN服务提供商是否使用了最新的协议,该公司的背景和声誉如何,服务条款是否容易理解,这些VPN 到底能防护什么和未能照顾到什么,它对于信息披露的细节表达了足够诚实吗?
抛开这些因素,Campbell建议大家看看公司的行为,他说这可能会显示出一个服务商是否关心客户的隐私。这三年来,他自己也在寻找一个清晰明确的隐私政策,而不是只有样板政策的公司。
Campbell警告道:
“在斯诺登泄密事件后,过去几年已有了很多廉价的VPN服务提供商。这些新入行的VPN服务提供商在安全方面做的不是很好。许多情况,他们想把部分服务器的主机业务转为带宽业务,但是他们完全没有安全方面的经验。”
作为最后一个预防措施,Campbell也在寻找不通过第三方系统捕获用户敏感数据的VPN,他表示:
“任何尊重客户隐私的VPN服务提供商,都不会去触碰与客户交互的系统,比如第三方聊天脚本、支持票务系统、博客评论等等。用户通常会在请求包里提交非常敏感的数据,但是他们并不一定清楚他们的VPN服务提供商是否单独监控了流量系统。”
自己动手,丰衣足食
根据你的隐私需求,一个满意的预解决方案可能并不存在。如果是这样的话,懂技术的用户可以自己搭建VPN。如果你的方案里更在意速度,你可以在DigitalOcean、Amazon主机、Vultur,、OVH或者其他可靠的主机商的VPS运行Streisand。Streisand是在土耳其推特全面被封杀后推出的,它的目的是为了帮助用户绕过互联网封锁。
Streisand的Github页面称:
“Streisand可以在服务器上搭建L2TP/IPsec、OpenConnect、OpenSSH、OpenVPN、Shadowsocks、sslh、Stunnel,以及Tor桥,它还会为这些服务生成自定义配置指令。”
其缔造者Joshua Lund告诉记者,Streisand的目标之一就是使得安装过程尽可能简单。他设想这个开源服务能够成长为一个“集中式知识存储库”,成为一个自动化升级最佳实践的社区。
Lund 在邮件中告诉记者:
“Streisand将几个最困难的步骤实现了自动化,大大提升了安全性。比如Streisand配置OpenVPN时会启用TLS认证(又名HMAC防火墙)”,生成了一个自定义组的Diffie-Hellman参数,启用了一个更强大的多密钥校验机制(AES-256/SHA-256替代了原来默认的Blowfish/SHA1)。许多用户在手动配置时,其实会跳过这些选择性的耗时步奏。事实上,大多数商业VPN服务商并不启用这些OpenVPN配置。
Streisand还有个好处在于,当自动安全更新和安装过程后,约十分钟就能让用户得到一个全新的服务。相比商业VPN服务商,Streisand也不太可能成为审查、DDoS或者流媒体封锁的目标。
像大多数VPN一样,Streisand会不同。在2016年考察这些产品后,我们只得到一条准则:寻找VPN决定于你使用它的第一目的。寻求对自身网络安全进行保护的用户,与那些想隐藏自己真实地址的用户目的是不同的。意识到VPN的局限性和具体的弱点缺陷,至少可以帮助你做出一个更明智的复杂决定。
*参考来源:ARS