So we have all heard of TOR in some way or another, whether it being the wrong doings on the dark web, and is usually associated with bad people that want to stay hidden. Although, we all have our own personal reasons for using TOR. In this video both me and Dale go over the fundamentals of TOR and explain the details of the networking, what to do and what not to do and the reason’s behind using it.
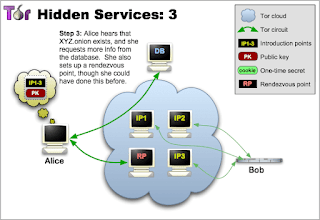 TOR nodes can be set up by anyone and there are loads of tutorials out there on how to do this. Although as anyone can set these up there are a few worries from the community. For example what if law enforcement was to set one of these TOR nodes and it so happened to be the last node. The good thing about TOR is that it uses multiple TOR nodes to anonymise you and the hops that are taken. So if a law enforcement was to have one TOR node that you went through. The other nodes would still mask your identity. However, if the law enforcement were to have 3 TOR nodes that you went through then you have issues, as each node would be under their control and would be able to identify the original source. The TOR community has thought about this and has come up with several solutions. Including guard nodes and bridge relays. Guard nodes which are “trusted nodes” which allow your traffic to pass through. Bridge relays are another way of getting on to TOR, however, these bridge relays need to be authorised from TOR to ensure that they are legitimate. In TOR’s documentation, they explain their hidden service protocol and how it works using “rendezvous points”
TOR nodes can be set up by anyone and there are loads of tutorials out there on how to do this. Although as anyone can set these up there are a few worries from the community. For example what if law enforcement was to set one of these TOR nodes and it so happened to be the last node. The good thing about TOR is that it uses multiple TOR nodes to anonymise you and the hops that are taken. So if a law enforcement was to have one TOR node that you went through. The other nodes would still mask your identity. However, if the law enforcement were to have 3 TOR nodes that you went through then you have issues, as each node would be under their control and would be able to identify the original source. The TOR community has thought about this and has come up with several solutions. Including guard nodes and bridge relays. Guard nodes which are “trusted nodes” which allow your traffic to pass through. Bridge relays are another way of getting on to TOR, however, these bridge relays need to be authorised from TOR to ensure that they are legitimate. In TOR’s documentation, they explain their hidden service protocol and how it works using “rendezvous points”
So TOR works completely different from how we normally use the internet. For example, if we wanted to go to demmsec.com we hop through different routers to get to the destination and the each hop can identify us. However if we wanted to use TOR not only do we use a completely different URL aka a onion address, but the method of reaching the onion site is different. We go through what’s called TOR nodes.
 TOR nodes can be set up by anyone and there are loads of tutorials out there on how to do this. Although as anyone can set these up there are a few worries from the community. For example what if law enforcement was to set one of these TOR nodes and it so happened to be the last node. The good thing about TOR is that it uses multiple TOR nodes to anonymise you and the hops that are taken. So if a law enforcement was to have one TOR node that you went through. The other nodes would still mask your identity. However, if the law enforcement were to have 3 TOR nodes that you went through then you have issues, as each node would be under their control and would be able to identify the original source. The TOR community has thought about this and has come up with several solutions. Including guard nodes and bridge relays. Guard nodes which are “trusted nodes” which allow your traffic to pass through. Bridge relays are another way of getting on to TOR, however, these bridge relays need to be authorised from TOR to ensure that they are legitimate. In TOR’s documentation, they explain their hidden service protocol and how it works using “rendezvous points”
TOR nodes can be set up by anyone and there are loads of tutorials out there on how to do this. Although as anyone can set these up there are a few worries from the community. For example what if law enforcement was to set one of these TOR nodes and it so happened to be the last node. The good thing about TOR is that it uses multiple TOR nodes to anonymise you and the hops that are taken. So if a law enforcement was to have one TOR node that you went through. The other nodes would still mask your identity. However, if the law enforcement were to have 3 TOR nodes that you went through then you have issues, as each node would be under their control and would be able to identify the original source. The TOR community has thought about this and has come up with several solutions. Including guard nodes and bridge relays. Guard nodes which are “trusted nodes” which allow your traffic to pass through. Bridge relays are another way of getting on to TOR, however, these bridge relays need to be authorised from TOR to ensure that they are legitimate. In TOR’s documentation, they explain their hidden service protocol and how it works using “rendezvous points”
Even if we was still paranoid and we thought that the TOR nodes were compromised, we can manually change the TOR route which will allow change to TOR nodes. There are methods to allow this to change automatically, and it is good practice to change these ever now and then.
There are loads of things that we should and shouldn’t do in order to achieve maximum anonymity. The first being not to maximise the TOR browser and the TOR browser even warns you that this is not a good idea. The information gathered from screen sizes and resolution can identify you more precisely and can be used in court as viable evidence. If you do intend on using TOR to do bad things then you obviously don’t want to sign into things like Facebook, twitter or anything that has your personal information. As mentioned in the video Facebook do have their own TOR service set up but I personally don’t like the idea of that. One last thing that we want to do is change the security settings that can be located within the onion button. We want to change this to high, this then stops any Javascript to run and enforces some HTML5 functions to be limited.
One last suggestion is to not copy your onion addresses into your normal browser as this will allow your ISP to then see what onion address you are trying to navigate too.
We can run our own services on TOR, it’s quite simple to do, in this video we use Kali, however, we can use whatever OS you choose. First, we need to install TOR
[bash]apt-get install -y tor[/bash]
[bash]apt-get install -y tor[/bash]
Then we need to install apache2 to host our service
[bash]apt-get install apache2[/bash]
[bash]apt-get install apache2[/bash]
Once that is installed then we can index.html file. In here we can add some simple text. “hi aron”
[bash] nano /var/www/html/index.html[/bash]
[bash] nano /var/www/html/index.html[/bash]
Then we need to edit the torrc file in order to enable a new hidden service.
[bash]nano /etc/tor/torrc[/bash]
[bash]nano /etc/tor/torrc[/bash]
Uncomment the lines
We then have to restart the TOR service
[bash]service tor restart[/bash]
[bash]service tor restart[/bash]
Then we can reveal the TOR onion address
[bash] cat /var/lib/tor/hidden_services/hostname[/bash]
[bash] cat /var/lib/tor/hidden_services/hostname[/bash]
Once we have the onion address we can then navigate to the website using our tor browser.

