传统防火墙会根据目标 IP
地址和端口号来屏蔽连接,但更高级的防火墙会使用深度包检测(DPI)技术或者状态包检测(SPI)技术来识别不同类型的加密算法和VPN协议。这就意味着它们能够检测出OpenVPN流量并将其标识出来,以方便管理员决定是否屏蔽目标服务器。
有三种方法可以绕过这种检测:使用混淆(obfuscation)代理,所使用的程序为obfsproxy;使用 SSL 通道(所使用的程序为stunnel)或者使用 SSH 通道。在本教程中,我们将讨论最后一种方法。SSH 通道会将你已经加密的链接封装在另一层加密中,这样防火墙就无法进行识别。这种方法可以用在绕过部署有完备 DPI 和 SPI 防火墙的公司或像天朝这种具有重度审查机制的国家。
但基于 SSH 通道的 OpenVPN 也有几个缺点。第一个就是双重加密必然会导致效率的降低。其次是虽然 OpenVPN 的指纹不在会被防火墙检出,但有些防火墙同样也会屏蔽 SSH 流量。就像 Netflix(美国一家在线影片租赁提供商) 会禁止使用任何类型加密代理的连接,无论是 OpenVPN、SSH 还是其他方式。在这种情况下,我们建议你使用混淆代理,其会使加密流量呈现出正常和未加密流量的样子。混淆代理非常强大,但为此付出的代价是,混淆代理难以的配置和运行。
但不幸的是,据我所知,具有混淆功能的OpenVPN 只能工作在桌面端,而使用 SSH 通道则还可以用在安卓或 IOS 等移动端。
本文假设你已经拥有一台配置好 OpenVPN 的服务器,并且能够通过 OpenVPN GUI 或者 APP 连接上服务器。同样的你也能够通过 SSH 连接上服务器,无论是使用 Mac 的终端还是在 PC 上使用 PuTTy。本文会以 PuTTy 进行演示。
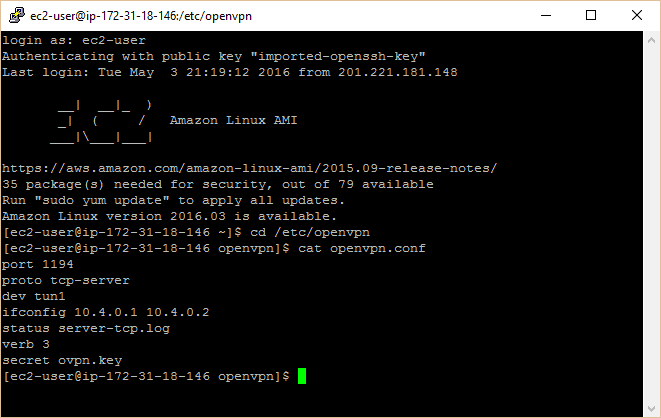
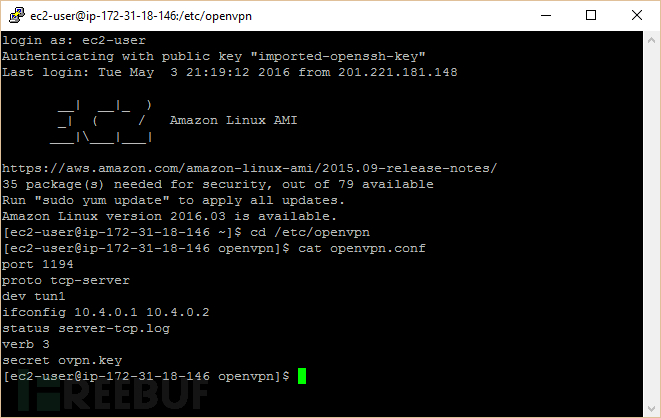
点击 “Open” 按钮登录到你的服务器,定位到 openvpn.conf 文件并使用如下命令检查配置:
复制一份原先的配置文件当备份,或者直接新建一个配置文件。使用记事本或者其他编辑器以管理员身份运行,打开或创建一个新的配置文件,如下所示:
将新的配置文件保存到 OpenVPN 的目录下面。
Firefox 中:
在开始前有几个注意事项。首先,此方法仅适用于浏览 Web。这是因为不像桌面端,在安卓或 IOS 设备上你无法随心所欲的打开端口,这意味着其他 Apps 无法直接使用 SSH 代理。为了解决这个问题,你可以选择进行 root 或越狱手机,然后使用像 ProxyDroid 或 Cydia’s Unix apps 来配置代理。
本教程以在安卓上面运行火狐浏览器为例,你需要安装如下应用:
找到电脑上的 ovpn.key 和 .ovpn 配置文件,将它们上传到手机上。同样的还有服务器主机的 .pem 密钥文件,这个文件应该位于与 .ppk 文件相同的文件夹下,用于 PuTTy 认证使用的。如果丢失了这个文件,你必须重新创建一个。
(可选)你也可以使用标准的 .ovpn 配置文件而不使用 SSH。这样你所有的 Apps 都就可以使用 VPN 连接上网,而不仅仅只限于浏览器,另外这样也可以用来进行排错。
在底部的 ssh 终端中输入你的 ssh 信息,像如下所示:
一旦你成功连接,再次点击右上角的三个点并断开连接。此时你的配置文件应该已经得以保存并显示在 ConnectBot 的主页上。长按配置文件打开菜单,在点击”编辑端口转发(Edit port forwards)”,然后在点击那三个点选择”增加端口转发(Add port forward)”。按你的喜好随意取个名字,随后选择类型为动态(SOCKS)端口为 8080,在点击”创建端口转发(create port forward)”。
这样 ConnectBot 就配置好了,但我们还没有创建连接,让我们来先配置好 OpenVPN 吧。
这时,在找到你的 ovpn.key 文件并选中,再点击右下角黄色的保存按钮。
这样你的新配置文件就应该出现在 App 的首页上了。
在连接前,让我们在检查下服务器的防火墙,在用户配置中赠加自定义的 TCP 规则,允许端口 22,1194和8080。
现在是时候开始连接了。首先打开 ConnectBot,选择我们刚才创建的 SSH 连接上服务器,确保公钥已经加载,不然会提示密码错误。在成功连接上后,切换到 OpenVPN App 选择你的配置文件进行连接。
当你连接上后,OpenVPN 日志末尾应该会显示为“CONNECTED,SUCCESS”。
请注意,因为我们使用了同电脑相同的 .pem 和 .key 文件,在同一时刻内你只能使用一台设备进行登录。当你想在移动端进行连接时,请确保电脑没有进行连接。如果你想同时连接多台设备,你需要为每一台设备生成新的凭证(.key 和 .pem)。
在 Firefox 的地址栏中,输入 “about:config”,然后在搜索栏中输入 “network.proxy”,这样我们就可以进行设置代理了,在相应的位置输入以下配置:
如果你只想通过 SSH 代理而不使用 OpenVPN 进行上网,只需要使用 ConnectBot SSH 登录服务器,同时不连接 OpenVPN 即可。同样的,如果你只想使用 OpenVPN 而不使用 SSH,则可以只导入基本的 .ovpn 配置文件使用 OpenVPN 进行连接,而不使用 SSH 通道。
原文:comparitech
--------------------------------
How to hide your OpenVPN traffic with an SSH tunnel
So you followed our tutorial on how to set up your own VPN server using OpenVPN and an Amazon EC2 server, and it was working great. That is, until it suddenly got blocked. Maybe you rebooted the instance and got a new IP address. It work great again for another couple days, then gets blocked. It seems your office, ISP, or government is actively blocking OpenVPN servers. So what do you do?
Basic firewalls block connections based on the port used and the destination IP address, but more advanced firewalls use deep packet inspection (DPI) and/or stateful packet inspection (SPI) to distinguish between different types of encryption algorithms and VPN protocols. That means they can detect OpenVPN traffic and flag it so the admin can block the server.
There are three options to get around this: an obfuscation proxy, SSL tunneling, and SSH tunneling. In this tutorial, we’ll discuss the lattermost. SSH tunneling wraps your already encrypted connection in another layer of encryption so the firewall can’t make the distinction. Each of these methods should bypass DPI and SPI firewalls put in place either by corporations or censorship-heavy governments like China’s.
OpenVPN over SSH does have a couple downsides. First is a performance hit due to the double encryption. Second, OpenVPN’s fingerprint can no longer be detected when tunneled through SSH, but some firewalls block SSH traffic as well. This is the case for services like Netflix, which halt the use of any type of encrypted proxy, OpenVPN, SSH, or otherwise. In this case, we recommend you set up Obfsproxy instead, which makes encrypted traffic appear to be normal and un-encrypted. Obfsproxy is much more powerful for this reason, but also more complicated to set up and run.
Unfortunately, Obfsproxy combined with OpenVPN currently only works on a desktop, so far as we are aware. SSH tunneling can be used on an Android or iOS mobile device.
This tutorial assumes you already have a functioning OpenVPN server set up and can connect to it using the OpenVPN GUI or OpenVPN Connect app. You must also be able to SSH into your server using either Terminal on a Mac or PuTTy on a PC. For demonstration purposes, we’ll be using PuTTy. If you don’t have all that set up, please refer to our previous tutorial.
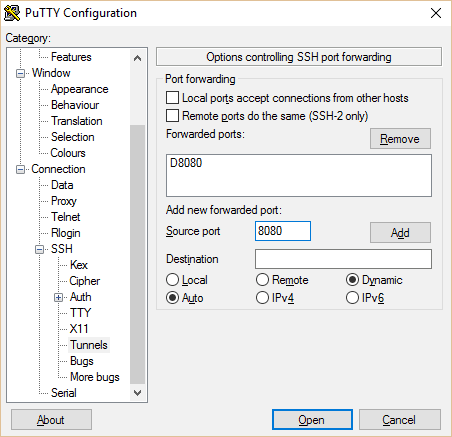
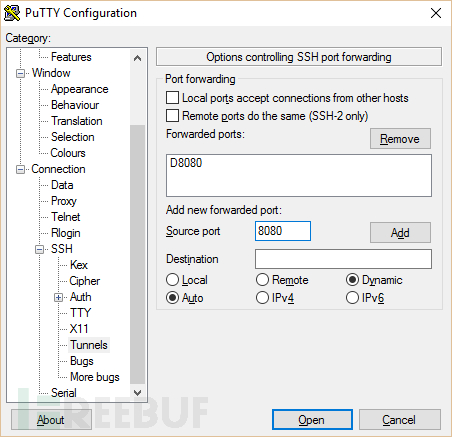
Open PuTTy and load up your VPN server configuration. In the sidebar, navigate to Connection > SSH > Tunnels. Make sure D8080 is included in the list. If not, type 8080 into “Source port” and check Auto and Dynamic. Then hit Add. You now have an SSH proxy running through port 8080. You can save this as a separate session configuration if you want back on the Session tab of the navigation tree.
Click Open and log into your server. Remember that on the newer Amazon Linux AMI, the username is “ec2-user”.
Navigate to your openvpn.conf file and check the contents using these commands
This should display the contents of your OpenVPN server configuration file. It should look like this:
The important thing is that the second line is set to TCP, not UDP. If you need to change it, you can edit it with this command:
Then click CTRL+O (the letter “o”, not zero) to save the file, then CTRL+X to exit the editor.
Create a copy of your existing OpenVPN config file from the last tutorial or create a new one. Find Notepad or another plain text editor and right click it to Run as administrator. Open or create your new config file, which should look like this:
Note the second “remote” line uses localhost instead of the OpenVPN server IP, plus the two lines on the end that configure OpenVPN to use a SOCKS proxy. Everything else is the same as before.
Save your new config file into the config folder of your OpenVPN directory.
In Firefox:
Now connect to your server first with PuTTy using the configuration above, then with the VPN using the new config file we created.
You are now connected to the internet with OpenVPN over SSH!
Before we begin, there are a couple caveats. First, this method only works for web browsing. That’s because, unlike a desktop, you can’t just open ports as you please on a stock Android or iOS device. That means the ports used by other apps won’t get directed through the SSH proxy. To overcome this, you can root or jailbreak your device and use an app like ProxyDroid or Cydia’s Unix apps to configure the proxy.
That’s a tutorial for a later day. For now, let’s get it up and running on stock Android with Firefox. You’ll need to install the following apps:
Locate your ovpn.key and the .ovpn config file you created above on your desktop, and move them onto your phone’s internal storage or SD card. Also move the .pem key file provided by your server host. It’s probably located in the same place as your .ppk file that you use to authenticate with PuTTy. If you’ve lost it, you’ll have to create another one on the Amazon EC2 dashboard, or from whichever server hosting service you use.
Optionally, you can grab the standard .ovpn config file that you use to connect without SSH. Then you can use your VPN with all apps instead of just the browser, and it’s useful for troubleshooting.
In the bottom terminal field next to “ssh”, input your SSH details. It should look like this:
Replace <your-server-IP> with the IP address of your OpenVPN server. Tap the enter key to SSH into your server. All this should be saved so you won’t have to re-enter it again, but you may need to toggle the public key again in the future.
Once you’ve successfully connected, hit the three dots again and disconnect. Your profile should be saved on the home screen of ConnectBot. Long press it to open a context menu, and tap “Edit port forwards.” On the next page, tap the three dots and choose “Add port forward.”
Name it whatever you like. Set Type to Dynamic (SOCKS) and source port to 8080 (or whatever is in the socks-proxy line of your OpenVPN config file). Tap “create port forward”.
ConnectBot is ready to go, but we won’t connect just yet. Let’s set up OpenVPN first.
Click the square button with a down-facing arrow on it in the top right corner to import a profile. Navigate to your .ovpn config file and select it. On the next page, hit the button that says “Select”.
This time, navigate to your ovpn.key file and select it. Hit the yellow save button on the bottom right hand corner.
Your new profile should now appear in the list on the home screen of the app.
Before we connect, let’s double-check our server firewall. Login to AWS, select Instances and highlight your OpenVPN server. In the Security Groups field, click the one used for this instance. Right click it and select “Edit Inbound Rules”.
Add Custom TCP rules for ports 22, 1194, and 8080, adjusting as necessary for your personal configuration.
Now, it’s time to connect. Open ConnectBot first. Tap the profile we just created to SSH into your server. Make sure the pubkey is toggled on, otherwise you’ll get an error about a password. After you’ve successfully connected, switch over to the OpenVPN app. Tap your profile there to connect.
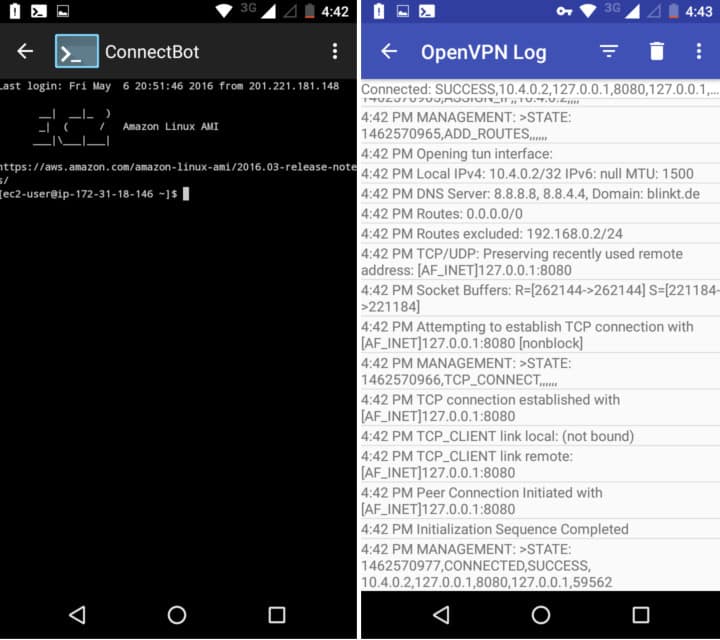
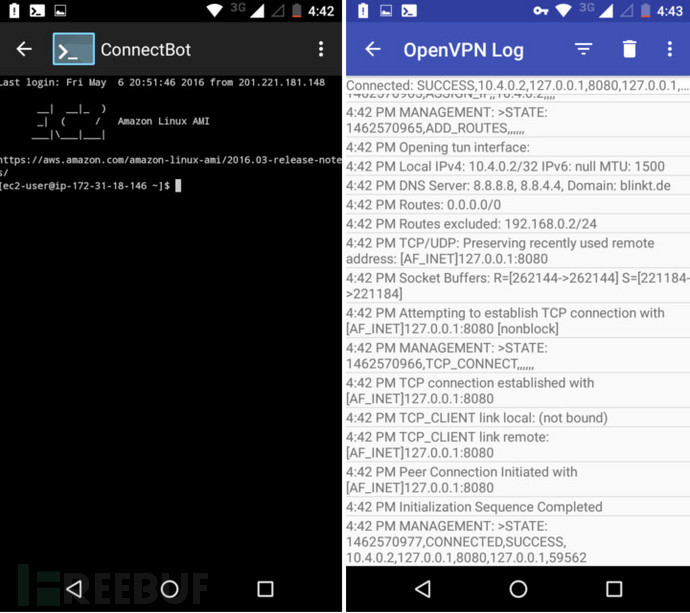
At the end of the OpenVPN log that pops up when you connect, you should see a message that says “CONNECTED,SUCCESS”.
Note that because we’re using the same .pem and .key files as on our desktop, you can only use these credentials on one device at a time. Make sure you aren’t connected on your desktop first. If you want to connect simultaneously on multiple devices, you’ll need to generate new credentials (.key and .pem) for each.
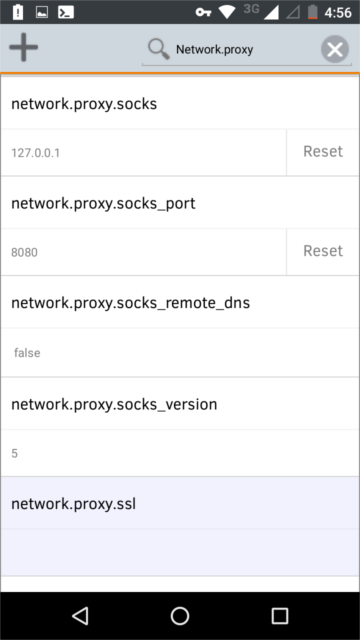
In the Firefox URL bar, type “about:config”. In the search bar on that page, type “network.proxy”. This will bring up all the fields we’re concerned with. Input the following settings on the indicated fields:
Should you want to connect through the SSH proxy without OpenVPN, just SSH into your server with ConnectBot and don’t connect with OpenVPN. Conversely, you can import your basic non-SSH .ovpn config file into the OpenVPN app and connect with that sans SSH proxy.
“tunnel” by jo.sau licensed under CC BY 2.0
有三种方法可以绕过这种检测:使用混淆(obfuscation)代理,所使用的程序为obfsproxy;使用 SSL 通道(所使用的程序为stunnel)或者使用 SSH 通道。在本教程中,我们将讨论最后一种方法。SSH 通道会将你已经加密的链接封装在另一层加密中,这样防火墙就无法进行识别。这种方法可以用在绕过部署有完备 DPI 和 SPI 防火墙的公司或像天朝这种具有重度审查机制的国家。
但基于 SSH 通道的 OpenVPN 也有几个缺点。第一个就是双重加密必然会导致效率的降低。其次是虽然 OpenVPN 的指纹不在会被防火墙检出,但有些防火墙同样也会屏蔽 SSH 流量。就像 Netflix(美国一家在线影片租赁提供商) 会禁止使用任何类型加密代理的连接,无论是 OpenVPN、SSH 还是其他方式。在这种情况下,我们建议你使用混淆代理,其会使加密流量呈现出正常和未加密流量的样子。混淆代理非常强大,但为此付出的代价是,混淆代理难以的配置和运行。
但不幸的是,据我所知,具有混淆功能的OpenVPN 只能工作在桌面端,而使用 SSH 通道则还可以用在安卓或 IOS 等移动端。
本文假设你已经拥有一台配置好 OpenVPN 的服务器,并且能够通过 OpenVPN GUI 或者 APP 连接上服务器。同样的你也能够通过 SSH 连接上服务器,无论是使用 Mac 的终端还是在 PC 上使用 PuTTy。本文会以 PuTTy 进行演示。
通过 SSH 配置 OpenVPN
打开 PuTTy 加载你的 VPN 服务器配置。在侧栏中选择 “Connection > SSH > Tunnels”,确保 D8080 包含在列表中。如果没有,那么如下图所示在 “Source port” 中输入8080,并选择 “Auto” 和 “Dynamic”,然后点击添加(Add)按钮。这样你就有了一个运行在 8080 端口的 SSH 代理了。如果你想保存设置,可以返回 “Session” 选项卡进行保存。点击 “Open” 按钮登录到你的服务器,定位到 openvpn.conf 文件并使用如下命令检查配置:
cd /etc/openvpn
cat openvpn.conf
port 1194
proto tcp-server
dev tun1
ifconfig 10.4.0.1 10.4.0.2
status server-tcp.log
verb 3
secret ovpn.keyxxxxxxxxxx
sudo nano openvpn.conf
客户端配置
在你的本地机器上,定位到 OpenVPN 客户端的配置文件。如果你使用默认的安装目录,那么应该在 “C:/Program Files/OpenVPN/config”。复制一份原先的配置文件当备份,或者直接新建一个配置文件。使用记事本或者其他编辑器以管理员身份运行,打开或创建一个新的配置文件,如下所示:
proto tcp-client
remote localhost 1194
port 1194
dev tun1
secret ovpn.key
redirect-gateway def1
ifconfig 10.4.0.2 10.4.0.1
socks-proxy-retry
socks-proxy 127.0.0.1 8080
将新的配置文件保存到 OpenVPN 的目录下面。
配置应用程序
最后一步就是配置你的应用程序使用 8080 端口的代理了。这跟配置基本的 SSH 代理步骤一样。许多应用又可以设置代理,有些甚至能够自动检测代理。如果你需要手动进行设置,下面三部分信息是你需要的:- Host: 127.0.0.1
- Port: 8080
- Proxy type: SOCKS5 (或者 SOCKS v5)
Firefox 中:
- 选择 “选项 > 高级 > 网络 > 连接 > 设置 > 手动设置代理”
- 设置 SOCKS 主机为 127.0.01 ,端口号设置为 8080 (或者你 PuTTy 里设置的端口号)
- 点击确定保存
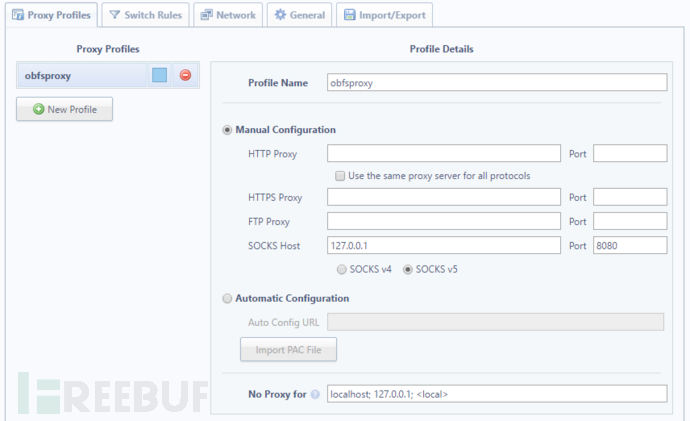
- 点击图标进入配置界面
- 随便命名一个新的模式,然后在人工配置下面,设置SOCKS 主机为 127.0.01 ,端口号设置为 8080 (或者你 PuTTy 里设置的端口号)
- 点击报错,然后切换使用新建的模式
译者注:Proxy Switchy已经停止更新了,Chrome 下面可以使用 SwitchyOmega,还是跟上面一样的配置。现在使用 PuTTy 连接到你的服务器,然后使用新的配置文件运行 VPN。这样你就可以使用基于 SSH 通道的 OpenVPN 上网了。
移动端
下面我们开始讲解如何在安卓上使用 OpenVPN+SSH,对于 IOS 端我们就不说了大同小异。在开始前有几个注意事项。首先,此方法仅适用于浏览 Web。这是因为不像桌面端,在安卓或 IOS 设备上你无法随心所欲的打开端口,这意味着其他 Apps 无法直接使用 SSH 代理。为了解决这个问题,你可以选择进行 root 或越狱手机,然后使用像 ProxyDroid 或 Cydia’s Unix apps 来配置代理。
本教程以在安卓上面运行火狐浏览器为例,你需要安装如下应用:
- OpenVPN for Android (注意不是OpenVPN Connect)
- ConnectBot 或者同样的 SSH 终端应用(JuiceSSH 挺不错的,但在转发端口上需要额外的开销)
- 一个文件管理器,例如:File Commander
- Firefox 或者其他能够配置代理的浏览器
找到电脑上的 ovpn.key 和 .ovpn 配置文件,将它们上传到手机上。同样的还有服务器主机的 .pem 密钥文件,这个文件应该位于与 .ppk 文件相同的文件夹下,用于 PuTTy 认证使用的。如果丢失了这个文件,你必须重新创建一个。
(可选)你也可以使用标准的 .ovpn 配置文件而不使用 SSH。这样你所有的 Apps 都就可以使用 VPN 连接上网,而不仅仅只限于浏览器,另外这样也可以用来进行排错。
配置ConnectBot
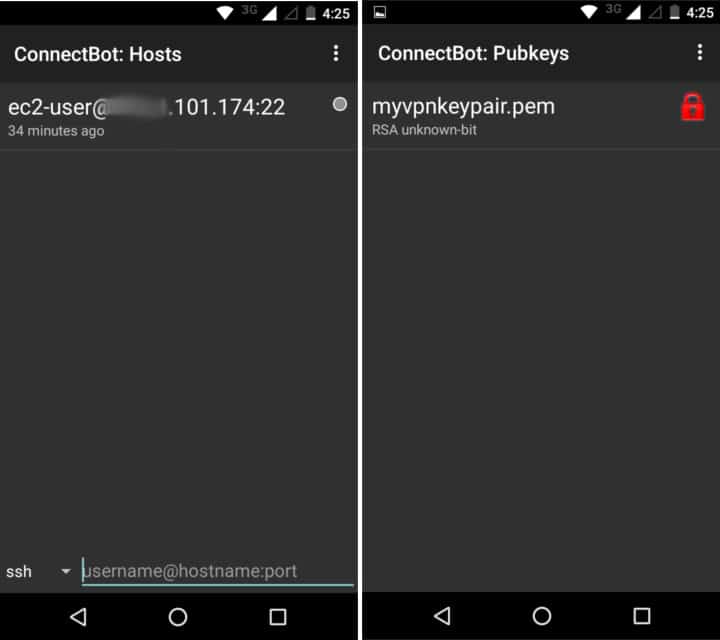
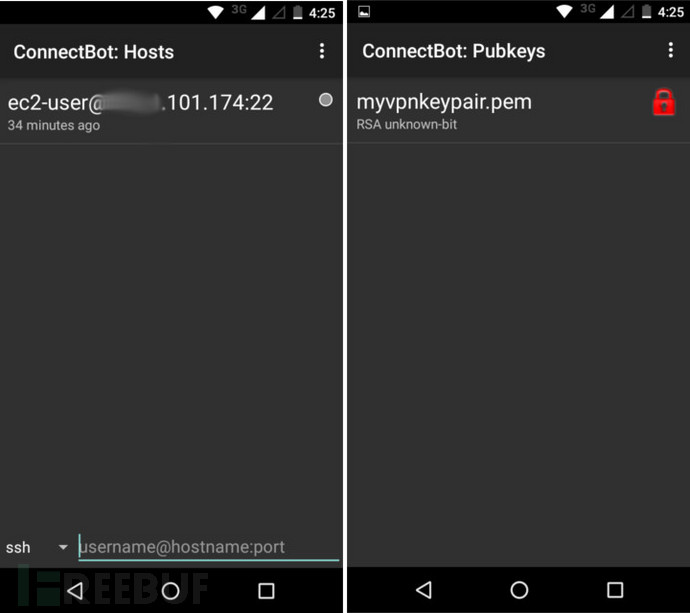
在手机上运行 ConnectBot,点击右上角的三个点进行管理公钥。再次点击第二页上面的点,然后点击导入,这样应该会启动你安装的文件管理器。找到上传的 .pem 文件并选择它,这样它应该会在公钥列表中出现并带有一个红色锁的标识。点击让其图标变绿,然后返回到 ConnectBot 主界面。在底部的 ssh 终端中输入你的 ssh 信息,像如下所示:
user@<your-server-IP>:22
一旦你成功连接,再次点击右上角的三个点并断开连接。此时你的配置文件应该已经得以保存并显示在 ConnectBot 的主页上。长按配置文件打开菜单,在点击”编辑端口转发(Edit port forwards)”,然后在点击那三个点选择”增加端口转发(Add port forward)”。按你的喜好随意取个名字,随后选择类型为动态(SOCKS)端口为 8080,在点击”创建端口转发(create port forward)”。
这样 ConnectBot 就配置好了,但我们还没有创建连接,让我们来先配置好 OpenVPN 吧。
配置OpenVPN for Android
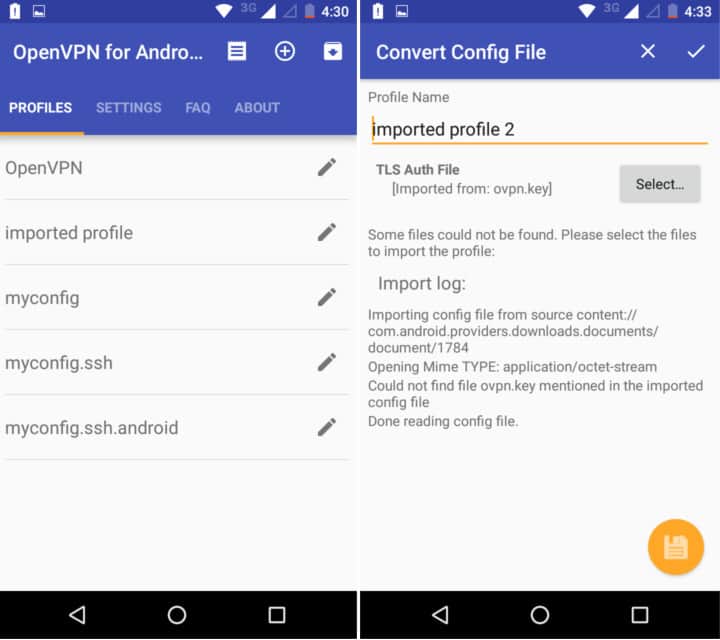
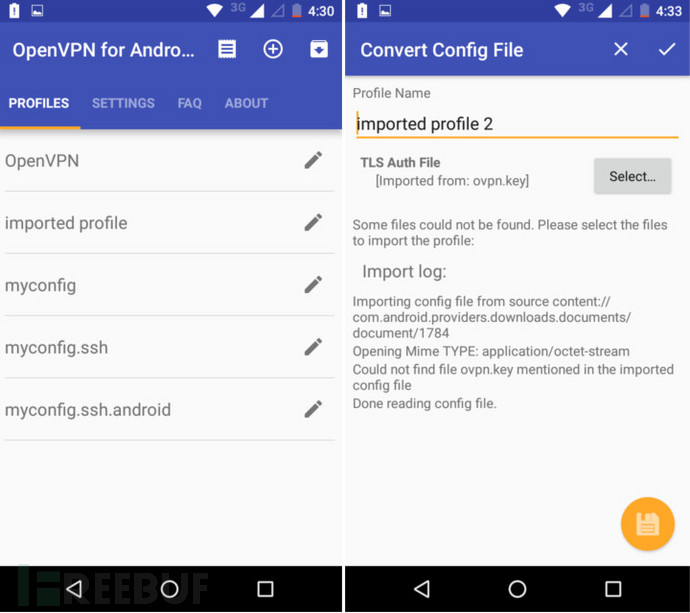
运行 OpenVPN for Android。点击右上角带有向下箭头的方形按钮进行导入配置。找到你的 .ovpn 配置文件并选中它。这时,在找到你的 ovpn.key 文件并选中,再点击右下角黄色的保存按钮。
这样你的新配置文件就应该出现在 App 的首页上了。
在连接前,让我们在检查下服务器的防火墙,在用户配置中赠加自定义的 TCP 规则,允许端口 22,1194和8080。
现在是时候开始连接了。首先打开 ConnectBot,选择我们刚才创建的 SSH 连接上服务器,确保公钥已经加载,不然会提示密码错误。在成功连接上后,切换到 OpenVPN App 选择你的配置文件进行连接。
当你连接上后,OpenVPN 日志末尾应该会显示为“CONNECTED,SUCCESS”。
请注意,因为我们使用了同电脑相同的 .pem 和 .key 文件,在同一时刻内你只能使用一台设备进行登录。当你想在移动端进行连接时,请确保电脑没有进行连接。如果你想同时连接多台设备,你需要为每一台设备生成新的凭证(.key 和 .pem)。
配置 Firefox 使用代理
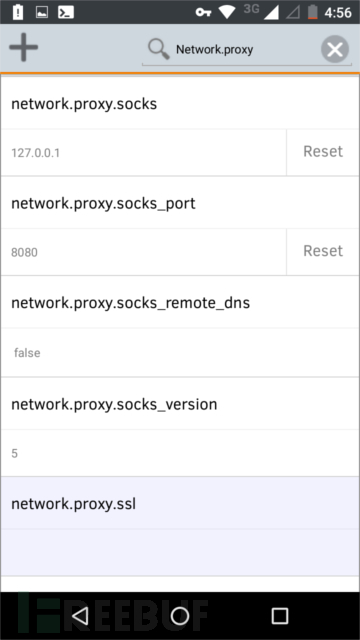
最后,我们需要配置 Firefox 使用代理。移动端的 Chrome 和 Safari 浏览器没有配置代理选项,这也是为什么我们推荐使用 Firefox。你可以在 wi-fi 环境下设置代理,但当你不再需要使用代理的时候要来回进行切换。在 Firefox 的地址栏中,输入 “about:config”,然后在搜索栏中输入 “network.proxy”,这样我们就可以进行设置代理了,在相应的位置输入以下配置:
- network.proxy.socks: 127.0.0.1
- network.proxy.socks_port: 8080 (或者你 PuTTy 里设置的端口号)
- network.proxy.type: 1
如果你只想通过 SSH 代理而不使用 OpenVPN 进行上网,只需要使用 ConnectBot SSH 登录服务器,同时不连接 OpenVPN 即可。同样的,如果你只想使用 OpenVPN 而不使用 SSH,则可以只导入基本的 .ovpn 配置文件使用 OpenVPN 进行连接,而不使用 SSH 通道。
原文:comparitech
--------------------------------
How to hide your OpenVPN traffic with an SSH tunnel
So you followed our tutorial on how to set up your own VPN server using OpenVPN and an Amazon EC2 server, and it was working great. That is, until it suddenly got blocked. Maybe you rebooted the instance and got a new IP address. It work great again for another couple days, then gets blocked. It seems your office, ISP, or government is actively blocking OpenVPN servers. So what do you do?
Basic firewalls block connections based on the port used and the destination IP address, but more advanced firewalls use deep packet inspection (DPI) and/or stateful packet inspection (SPI) to distinguish between different types of encryption algorithms and VPN protocols. That means they can detect OpenVPN traffic and flag it so the admin can block the server.
There are three options to get around this: an obfuscation proxy, SSL tunneling, and SSH tunneling. In this tutorial, we’ll discuss the lattermost. SSH tunneling wraps your already encrypted connection in another layer of encryption so the firewall can’t make the distinction. Each of these methods should bypass DPI and SPI firewalls put in place either by corporations or censorship-heavy governments like China’s.
OpenVPN over SSH does have a couple downsides. First is a performance hit due to the double encryption. Second, OpenVPN’s fingerprint can no longer be detected when tunneled through SSH, but some firewalls block SSH traffic as well. This is the case for services like Netflix, which halt the use of any type of encrypted proxy, OpenVPN, SSH, or otherwise. In this case, we recommend you set up Obfsproxy instead, which makes encrypted traffic appear to be normal and un-encrypted. Obfsproxy is much more powerful for this reason, but also more complicated to set up and run.
Unfortunately, Obfsproxy combined with OpenVPN currently only works on a desktop, so far as we are aware. SSH tunneling can be used on an Android or iOS mobile device.
This tutorial assumes you already have a functioning OpenVPN server set up and can connect to it using the OpenVPN GUI or OpenVPN Connect app. You must also be able to SSH into your server using either Terminal on a Mac or PuTTy on a PC. For demonstration purposes, we’ll be using PuTTy. If you don’t have all that set up, please refer to our previous tutorial.
Setting up OpenVPN over SSH on a PC
In our last tutorial, we discussed how to set up a simple SSH proxy, then expanded on that to create a full-on VPN server. This approach combines the two, which means you should already have everything you need.Open PuTTy and load up your VPN server configuration. In the sidebar, navigate to Connection > SSH > Tunnels. Make sure D8080 is included in the list. If not, type 8080 into “Source port” and check Auto and Dynamic. Then hit Add. You now have an SSH proxy running through port 8080. You can save this as a separate session configuration if you want back on the Session tab of the navigation tree.

Click Open and log into your server. Remember that on the newer Amazon Linux AMI, the username is “ec2-user”.
Navigate to your openvpn.conf file and check the contents using these commands
cd /etc/openvpn
cat openvpn.conf This should display the contents of your OpenVPN server configuration file. It should look like this:
port 1194
proto tcp-server
dev tun1
ifconfig 10.4.0.1 10.4.0.2
status server-tcp.log
verb 3
secret ovpn.key
The important thing is that the second line is set to TCP, not UDP. If you need to change it, you can edit it with this command:
sudo nano openvpn.conf Then click CTRL+O (the letter “o”, not zero) to save the file, then CTRL+X to exit the editor.
Client config
On your local machine, navigate to your OpenVPN client config files. If you used the default installation directory, this will be C:/Program Files/OpenVPN/config.Create a copy of your existing OpenVPN config file from the last tutorial or create a new one. Find Notepad or another plain text editor and right click it to Run as administrator. Open or create your new config file, which should look like this:
proto tcp-client
remote localhost 1194
port 1194
dev tun1
secret ovpn.key
redirect-gateway def1
ifconfig 10.4.0.2 10.4.0.1
socks-proxy-retry
socks-proxy 127.0.0.1 8080 Note the second “remote” line uses localhost instead of the OpenVPN server IP, plus the two lines on the end that configure OpenVPN to use a SOCKS proxy. Everything else is the same as before.
Save your new config file into the config folder of your OpenVPN directory.
Setting up apps
The last step is to configure your apps to use the proxy over port 8080. This is similar to what we did with the basic SSH proxy from the last tutorial. Many apps will have a proxy setup available in the settings, and some may even auto-detect it. If you need to set it up manually, the three pieces of information you need are:- Host: 127.0.0.1
- Port: 8080
- Proxy type: SOCKS5 (or SOCKS v5)
In Firefox:
- Go to Tools > Options > Advanced > Network > Connection > Settings > Manual proxy configuration
- Set SOCKS Host as 127.0.0.1 and the port as 8080 (or whatever you set the tunnel port to on PuTTy).
- Click OK to save
- A setup page should appear as soon as you install the extension, or click the icon in the top right of Chrome and click Options.
- Name the profile whatever you like. Under Manual Configuration, set the SOCKS host to 127.0.0.1 and the port to 8080 (or whatever you set the tunnel port to in PuTTy. Leave everything else blank.
- Hit Save, then click the icon again to select your proxy profile.

Now connect to your server first with PuTTy using the configuration above, then with the VPN using the new config file we created.
You are now connected to the internet with OpenVPN over SSH!
Mobile
We’re going to explain how to adapt your OpenVPN+SSH tunnel for Android, though iOS shouldn’t be all that different.Before we begin, there are a couple caveats. First, this method only works for web browsing. That’s because, unlike a desktop, you can’t just open ports as you please on a stock Android or iOS device. That means the ports used by other apps won’t get directed through the SSH proxy. To overcome this, you can root or jailbreak your device and use an app like ProxyDroid or Cydia’s Unix apps to configure the proxy.
That’s a tutorial for a later day. For now, let’s get it up and running on stock Android with Firefox. You’ll need to install the following apps:
- OpenVPN for Android (note: NOT OpenVPN Connect, which is more picky about authentication)
- ConnectBot, or an equivalent SSH terminal app (JuiceSSH is good but costs extra to forward ports)
- A file manager such as File Commander
- Firefox, or another browser that lets you configure proxies
Locate your ovpn.key and the .ovpn config file you created above on your desktop, and move them onto your phone’s internal storage or SD card. Also move the .pem key file provided by your server host. It’s probably located in the same place as your .ppk file that you use to authenticate with PuTTy. If you’ve lost it, you’ll have to create another one on the Amazon EC2 dashboard, or from whichever server hosting service you use.
Optionally, you can grab the standard .ovpn config file that you use to connect without SSH. Then you can use your VPN with all apps instead of just the browser, and it’s useful for troubleshooting.
ConnectBot setup
Run ConnectBot on your phone. Click the three dots on the top right hand corner, and go to Manage Pubkeys. Click the dots again on the next page, and click Import. This should launch the file manager you installed. Find the .pem file you just moved onto your phone and select it. It should now appear in the list of public keys with a red lock next to it. Tap it so it turns green. Hit the back button to go back to the main page on ConnectBot.
In the bottom terminal field next to “ssh”, input your SSH details. It should look like this:
ec2-user@<your-server-IP>:22 Replace <your-server-IP> with the IP address of your OpenVPN server. Tap the enter key to SSH into your server. All this should be saved so you won’t have to re-enter it again, but you may need to toggle the public key again in the future.
Once you’ve successfully connected, hit the three dots again and disconnect. Your profile should be saved on the home screen of ConnectBot. Long press it to open a context menu, and tap “Edit port forwards.” On the next page, tap the three dots and choose “Add port forward.”
Name it whatever you like. Set Type to Dynamic (SOCKS) and source port to 8080 (or whatever is in the socks-proxy line of your OpenVPN config file). Tap “create port forward”.
ConnectBot is ready to go, but we won’t connect just yet. Let’s set up OpenVPN first.
OpenVPN for Android setup
Run OpenVPN for Android.Click the square button with a down-facing arrow on it in the top right corner to import a profile. Navigate to your .ovpn config file and select it. On the next page, hit the button that says “Select”.

This time, navigate to your ovpn.key file and select it. Hit the yellow save button on the bottom right hand corner.
Your new profile should now appear in the list on the home screen of the app.
Before we connect, let’s double-check our server firewall. Login to AWS, select Instances and highlight your OpenVPN server. In the Security Groups field, click the one used for this instance. Right click it and select “Edit Inbound Rules”.
Add Custom TCP rules for ports 22, 1194, and 8080, adjusting as necessary for your personal configuration.
Now, it’s time to connect. Open ConnectBot first. Tap the profile we just created to SSH into your server. Make sure the pubkey is toggled on, otherwise you’ll get an error about a password. After you’ve successfully connected, switch over to the OpenVPN app. Tap your profile there to connect.

At the end of the OpenVPN log that pops up when you connect, you should see a message that says “CONNECTED,SUCCESS”.
Note that because we’re using the same .pem and .key files as on our desktop, you can only use these credentials on one device at a time. Make sure you aren’t connected on your desktop first. If you want to connect simultaneously on multiple devices, you’ll need to generate new credentials (.key and .pem) for each.
Configure Firefox to use a proxy
Finally, we need to configure Firefox to use the proxy. Chrome and Safari on mobile don’t come with proxy configuration options, which is why we recommend Firefox. You can try setting up the proxy in the wi-fi settings, but then you’ll have to change them every time you want to connect without a proxy.
In the Firefox URL bar, type “about:config”. In the search bar on that page, type “network.proxy”. This will bring up all the fields we’re concerned with. Input the following settings on the indicated fields:
- network.proxy.socks: 127.0.0.1
- network.proxy.socks_port: 8080 (or whatever you set in your OpenVPN config and ConnectBot)
- network.proxy.type: 1
Should you want to connect through the SSH proxy without OpenVPN, just SSH into your server with ConnectBot and don’t connect with OpenVPN. Conversely, you can import your basic non-SSH .ovpn config file into the OpenVPN app and connect with that sans SSH proxy.
“tunnel” by jo.sau licensed under CC BY 2.0
Am I missing something?
Thanks,
Eric
can you show a configuration if not using the amazon server, im using vps server that i just brought from a hosting company
A VPS is a bit different than a VPN, although in this case they can both serve the same purpose. I don’t have a VPS set up for myself at the moment, so I can’t give you a working config.
Best,
Paul
—
Sam Smith
Technology Evangelist and Aspiring Chef.
Large file transfers made easy.
http://www.innorix.com/en/DS
I’m glad the tutorial was helpful. I’m not sure why your VPN would score so low without seeing the full report. I just tried it with NordVPN and scored 99%.
Best,
Paul
Thanks for the wonderful tutorial. Can you make the configuration using only “openvpn for android” for android mobile phone. Or what if i use only the”openvpn for android” for this.
Thank You Paul, May God bless you.
You could use OpenVPN Connect but it handles authentication a bit differently, which makes it a pain. I found OpenVPN for Android much easier to set up.
What do you mean” app like ProxyDroid or Cydia’s Unix apps to configure the proxy”?
I search in Cydia but even one app is called Unix.. I know that for android there is Proxydroid but what can I use for Iphone? I’m searching for months and months..Thanks for helping!
[…]That means the ports used by other apps won’t get directed through the SSH proxy. To overcome this, you can root or jailbreak your device and use an app like ProxyDroid or Cydia’s Unix apps to configure the proxy[…]
I’m not terribly familiar with the Cydia repository as I don’t have an unlocked iPhone to test it with, but try looking for a terminal app that allows you to navigate send send commands to the OS in the same way that you would a Unix terminal (i.e. the same way you interact with your server). You must be able to log in as root to do so as well.
Best,
Paul
from https://www.comparitech.com/blog/vpn-privacy/hide-openvpn-traffic-with-ssh-tunnel/