Malware is malicious software that
acts counter to the interests of the computer that hosts it. Viruses,
worms, and Trojans are all types of malware.
The standard way that a device gets infected by malware is through an
executable program copied onto the victim’s machine. That file is often
disguised as a different file format such as a PDF or JPEG, or it is
hidden inside a carrying file like a compressed zip file.
See also: Complete Guide to Windows Malware Removal and Prevention
However, the fileless system doesn’t involve a second program downloaded by a malware installer. Instead, resident, trusted programs execute in a manner that makes them perform maliciously. The computer service that made fileless malware possible is Microsoft’s PowerShell.
The off-the-shelf method of creating fileless attack has seen an explosion in this type of malware. The Ponemon Institute’s “The State of Endpoint Security Risk Report” estimates 77 percent of detected attacks in 2017 were fileless. The authors of the report believe fileless attacks are ten times more successful than file-based attacks.
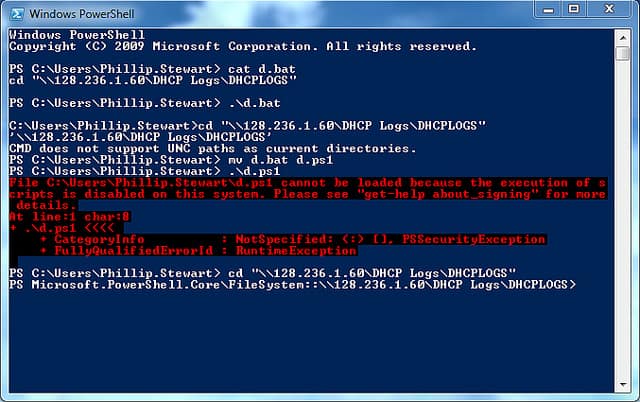
PowerShell is a script interpreter. A script is a collection of commands that can be executed individually by typing them in. However, when you write a plain text file that contains a series of operating system commands, it becomes a script. A script won’t do anything if you just click on it. In its basic state, the script is just a plain text file. Instead, in you need to pass the script as a parameter to an interpreter program. The interpreter then reads through the file and executes each command contained within.
The PowerShell program runs in system memory that cannot be queried or searched, so that makes malicious PowerShell activities almost impossible to detect. PowerShell has full access to the core operating system of a Windows computer, so it can wreak total havoc because by undermining all security features, such as user accounts. It can even manipulate the definition of user accounts and password protection.
Another native program that can be used for fileless attacks is the Windows Management Instrumentation (WMI). The use of WMI is to carry commands to PowerShell. An example of a useful function that WMI can perform for a fileless hacker is the ability to wake up WinRM if it has been turned off on a machine. WMI also provides the hacker with access to the registry of a computer.
We’ve covered PowerShell in more detail in our PowerShell cheat sheet article.
The JavaScript that creates fileless malware calls on PowerShell and feeds it a series of commands. Each command executes in memory without having to bounce through a file on the disk. Once all of the commands have been run, the JavaScript closes down the PowerShell window and there is no trace that a script was run. Although the code for the web page will be stored on the disk temporarily while it loads into the browser, when that web page is closed down, the code that created it is wiped out.
The fact that the damage done by fileless malware is performed by instructions sent to native programs, rather than from malicious code, gives this type of intrusion the name of “non-malware attack.”
Short lists of instructions don’t have to be stored in a file. However, longer and more complicated scripts do get stored for relaunch at system start up. In these case, although the program is classified as “fileless,” there is actually a file involved.
Frodo was discovered in October 1989. It was relatively harmless in that it was a prank rather than a destructive piece of code. Its aim was to flash the message “Frodo Lives” on the screen of the infected computer. However, the program was so badly written that it did have the potential to accidentally damage its host.
Its aim was to infect executable files whenever they were run on an infected computer. It would even infect files whenever they were copied. The creator of this virus became known as Dark Avenger.
This virus was named Duqu 2.0 by Kaspersky Researchers, who calculated that the virus had gone undetected on the network for at least six months. The characteristics of Duqu 2.0 identified it as a variation on Stuxnet, which was created by the US and Israeli secret services.
The malware was executed on the system of an Asian corporation and the PowerShell scripts involved were able to communicate with an external command and control server. This enabled it to initiate a series of attacks, which included the Cobalt Strike Beacon virus.
This attacked aimed to control ATM machines and facilitate a cash robbery. The discovery of the malware thwarted the attempted heist in all but one country. Hackers in Russia managed to control the ATMs of eight bank branches and withdraw $800,000. Kaspersky Labs discovered this stealth attack when it was called in by an infected bank to investigate the intrusion.
The urgency with which owners of XP machines closed off this exploit by installing the patch meant that there were few vulnerable computers left by the time UIWIX launched. UIWIX is an example of how Eternal Blue is increasingly being used in fileless attacks. This is a ransom attack with demands written in English. The program will not run in Russia, Kazakhstan, or Belarus.
Thanks to the stealth of the no-malware model, many of these infections persist for months. The virus was first spotted running in memory without any trace of a file-based program in mid-2017, and new infections are ongoing. The purpose of WannaMine is the creation of Monero.
The creators of Misfox had the misfortune of getting their malware spotted by a key Microsoft security team. This led to Microsoft bundling a solution to this malware in Windows Defender.
The system processes used by fileless malware are so essential to Microsoft’s operating systems and Windows software developers that they cannot be turned off without losing most of a business’s IT infrastructure software capabilities.
Therefore, Microsoft upgraded its Windows Defender package to detect irregular activity from PowerShell and WMI. Fine tuning Windows Defender enabled Microsoft to double the number of incidents that the firewall blocked in Q2 2017 compared to the previous quarter. That success against Misfox would also trap other viruses that exploit PowerShell.
As fileless malware almost exclusively attacks Windows, this is a Microsoft problem and the company’s response should rapidly reduce the threat of no-malware attacks.
Other measures that you can take to block fileless malware intrusion are:
Also, caution workers against opening attachments in emails not sent from trusted sources. Two types of documents are particularly hazardous:
If a PDF is downloaded before it is opened, your firewall has a chance to spot any malicious code within. Also, one of the problems of tracing a fileless attack is working out where it originated from. If the file is downloaded, it is available for analysis later. That is preferable to the disappearing malicious code that leaves no trace of its existence once the PDF viewing tab in the browser is closed.
Disable the ability of PDFs to load in browsers. You should also disable your PDF readers from activating JavaScript.
A macro attack is not really a fileless malware conduit. However, the online availability of Microsoft products, including viewers for productivity documents for those who do not possess the Office suite, creates opportunities to run macros in the browser and launch calls to PowerShell or WMI.
Just like its Adobe stablemate, PDF, the web video delivery system Flash has become known as a malware-friendly feature in a web page. Most websites have already stripped out Flash and replaced it with HTML5 for video inclusion. Therefore, it is no great hardship to block this system from appearing in your browsers.
Read more here on why Flash is not secure.
The ability to deliver code through browsers should make fileless malware very easy to adapt to other operating systems. The only issue hackers face when porting this attack strategy is the need to discover an equivalent service on Linux and Macs that will match the usefulness of PowerShell. The fact that they haven’t found that facility yet is probably because they are so busy exploiting PowerShell right now.
from https://www.comparitech.com/blog/information-security/fileless-malware-attacks/
Is fileless malware a virus?
When malware is executed, the instructions of the file are loaded into memory. It is that active process that causes the damage. Fileless malware is the same as a traditional virus in that it is a process that operates in memory. The difference between this new type of malware and traditional viruses is that the code for fileless malware is not stored in a file nor installed on the victim’s machine. Fileless malware loads directly into memory as system commands and runs immediately. Often it will continue to run until the host device is powered down — putting a computer into standby mode won’t kill off the malware process. The vast majority of fileless malware targets Windows computers.See also: Complete Guide to Windows Malware Removal and Prevention
Fileless malware origins
No one knows who invented the concept of fileless malware. However, this operating type first emerged in 2017. Early examples of this malware were Frodo, Number of the Beast, and The Dark Avenger.The meaning of “fileless”
Although the fileless model is new, it builds on standard malware techniques that have been in operation since the 1990s. It would be difficult to load a program into memory without any file at all. The actual operation of the installation is managed by a separate program, which does involve a file. The strategy of bundling together specialized malware programs is common practice in Trojan architecture.However, the fileless system doesn’t involve a second program downloaded by a malware installer. Instead, resident, trusted programs execute in a manner that makes them perform maliciously. The computer service that made fileless malware possible is Microsoft’s PowerShell.
Why now?
Fileless malware attacks have become more prevalent since 2017 thanks to the creation of attack kits that integrate calls to PowerShell. These kits are virus creation environments. Fileless frameworks include Empire and PowerSploit. These kits create the intrusion phase of an attack. Attack frameworks that create intrusive and damaging PowerShell scripts for delivery later include Metasploit and CobaltStrike.The off-the-shelf method of creating fileless attack has seen an explosion in this type of malware. The Ponemon Institute’s “The State of Endpoint Security Risk Report” estimates 77 percent of detected attacks in 2017 were fileless. The authors of the report believe fileless attacks are ten times more successful than file-based attacks.
About PowerShell

PowerShell is a script interpreter. A script is a collection of commands that can be executed individually by typing them in. However, when you write a plain text file that contains a series of operating system commands, it becomes a script. A script won’t do anything if you just click on it. In its basic state, the script is just a plain text file. Instead, in you need to pass the script as a parameter to an interpreter program. The interpreter then reads through the file and executes each command contained within.
The PowerShell program runs in system memory that cannot be queried or searched, so that makes malicious PowerShell activities almost impossible to detect. PowerShell has full access to the core operating system of a Windows computer, so it can wreak total havoc because by undermining all security features, such as user accounts. It can even manipulate the definition of user accounts and password protection.
Should I delete Powershell?
PowerShell is very useful and it is widely used by a lot of standard programs, particularly Microsoft utilities. The program can be run remotely, and it can also execute commands on other computers to which the host computer is connected via a network or the internet. The remote execution functions of PowerShell are actually managed by another native Windows tool, called WinRM. PowerShell routines are not blocked by firewalls or antivirus programs because they are ubiquitous in modern IT environments and blocking them would shut down a large segment of network activity.Another native program that can be used for fileless attacks is the Windows Management Instrumentation (WMI). The use of WMI is to carry commands to PowerShell. An example of a useful function that WMI can perform for a fileless hacker is the ability to wake up WinRM if it has been turned off on a machine. WMI also provides the hacker with access to the registry of a computer.
We’ve covered PowerShell in more detail in our PowerShell cheat sheet article.
Executing fileless malware
The installing program that starts up fileless malware does not have to be resident on a computer for long. It is not expected to endure on the host device. Instead, a common delivery method to launch fileless malware programs is through web pages.Web-based launches
A web page is written in HTML. This is just a formatting language with no programming capabilities. So, a number of scripting languages came along that enable program functions to be executed within web pages. JavaScript is an example of a web scripting language. It is very normal for a web page to include JavaScript, and anti-malware programs rarely attempt to analyze it.The JavaScript that creates fileless malware calls on PowerShell and feeds it a series of commands. Each command executes in memory without having to bounce through a file on the disk. Once all of the commands have been run, the JavaScript closes down the PowerShell window and there is no trace that a script was run. Although the code for the web page will be stored on the disk temporarily while it loads into the browser, when that web page is closed down, the code that created it is wiped out.
Other carriers
Another common carrier of fileless malware is the Flash video playing system. Macros in Microsoft Office tools can also be used by hackers to deliver fileless malware.The fact that the damage done by fileless malware is performed by instructions sent to native programs, rather than from malicious code, gives this type of intrusion the name of “non-malware attack.”
Fileless malware persistence
When you turn off a computer, all active processes shut down. Processes that are services of the operating system are started up again when you turn the computer on. You have to wait a while between clicking the power button on your computer and the point at which the Desktop is loaded and you can start opening applications. Even once the Desktop is ready, you will notice that your computer is still very busy as it continues to start up background processes.Persistence scripts
Fileless malware writes its script into the Registry of Windows. This is a function of the operating system that launches programs either at system startup or on a schedule. The code that runs the fileless malware is actually a script. A script is a plain text list of commands, rather than a compiled executable file.Short lists of instructions don’t have to be stored in a file. However, longer and more complicated scripts do get stored for relaunch at system start up. In these case, although the program is classified as “fileless,” there is actually a file involved.
Process identifiers
As the fileless malware launches programs native to the operating system instead of its own program, the operations of those instructions do not show up in Task Manager under the name of the malware program. Instead, anyone examining active processes will see the name of the interface that managed the launch of the script, such as PowerShell, and then see the common processes operating under their own name.Fileless malware attacks
The fileless malware phenomenon is relatively recent, and so there have not yet been many examples of them. However, here are some of the attacks that have taken place since 2017.Frodo
Although Frodo wasn’t a truly a fileless virus, it is included in this list as it is considered to be one of the forerunners of the genre. The aspect of the virus that marks it out as a precursor to fileless malware is that it loaded into the boot sector of a computer.Frodo was discovered in October 1989. It was relatively harmless in that it was a prank rather than a destructive piece of code. Its aim was to flash the message “Frodo Lives” on the screen of the infected computer. However, the program was so badly written that it did have the potential to accidentally damage its host.
The Dark Avenger
This is another pre-cursor to the fileless virus methodology, and it was first discovered in September 1989. This virus required a file as a delivery system, but then operated in memory.Its aim was to infect executable files whenever they were run on an infected computer. It would even infect files whenever they were copied. The creator of this virus became known as Dark Avenger.
Duqu 2.0
Moscow-based Kaspersky Labs has risen to be one of the foremost anti-malware producers in the world. In 2015 they discovered one of the first fileless malware infections attacking their own IT system.This virus was named Duqu 2.0 by Kaspersky Researchers, who calculated that the virus had gone undetected on the network for at least six months. The characteristics of Duqu 2.0 identified it as a variation on Stuxnet, which was created by the US and Israeli secret services.
Operation Cobalt Kitty
This was an advanced persistent threat that endured for at least a year before it was detected in May 2017.The malware was executed on the system of an Asian corporation and the PowerShell scripts involved were able to communicate with an external command and control server. This enabled it to initiate a series of attacks, which included the Cobalt Strike Beacon virus.
Meterpreter
The Meterpreter program found its way into the memory of computers at more than 100 banks spread across 40 countries in February 2017. Meterpreter is an onboard element of the malware kit, called Metasploit.This attacked aimed to control ATM machines and facilitate a cash robbery. The discovery of the malware thwarted the attempted heist in all but one country. Hackers in Russia managed to control the ATMs of eight bank branches and withdraw $800,000. Kaspersky Labs discovered this stealth attack when it was called in by an infected bank to investigate the intrusion.
UIWIX
The WannaCry ransomware attack in May 2017 attracted a lot of media coverage. UIWIX was rolled out shortly afterwards, but with less success. UIWIX uses the same exploit as WannaCry, which is called Eternal Blue. However, it has a fileless execution system. The publicity that surrounded the rollout of WannaCry prompted Microsoft to come up with a patch that resolved a weakness in the XP version of Windows.The urgency with which owners of XP machines closed off this exploit by installing the patch meant that there were few vulnerable computers left by the time UIWIX launched. UIWIX is an example of how Eternal Blue is increasingly being used in fileless attacks. This is a ransom attack with demands written in English. The program will not run in Russia, Kazakhstan, or Belarus.
WannaMine
The Eternal Blue exploit is also used by hacker cryptocurrency miners and directed at the large servers of corporations. This fileless malware mines cryptocurrency on the host computer.Thanks to the stealth of the no-malware model, many of these infections persist for months. The virus was first spotted running in memory without any trace of a file-based program in mid-2017, and new infections are ongoing. The purpose of WannaMine is the creation of Monero.
Misfox
Misfox was first identified by the Microsoft Incident Response team in April 2016. Misfox uses the classic fileless techniques of executing commands through PowerShell and achieving persistence through Registry infection.The creators of Misfox had the misfortune of getting their malware spotted by a key Microsoft security team. This led to Microsoft bundling a solution to this malware in Windows Defender.
Fileless malware trends
Although there was a marked increase in the number of fileless malware attacks at the beginning of 2017, the success of this technique seems to be waning. The 2017 surge was due to the discovery and definition of the technique and its formulation into hacker toolkits, which made the methodology easy to implement.Malware lifecycle
The marked lack of success of UIWIX in comparison to its immediate predecessor WannaCry shows the most effective hacker techniques are new ones. The speed at which the cybersecurity industry now rushes to close off exploits considerably shortens the attack life of new viruses and infection methods.Defense response
Although fileless malware is harder to detect than traditional file-based infections, the specific targeting of Windows services has laid a challenge to Microsoft, and they met that challenge full on. The response to no-malware attacks has come from Microsoft itself rather than from the anti-malware industry.The system processes used by fileless malware are so essential to Microsoft’s operating systems and Windows software developers that they cannot be turned off without losing most of a business’s IT infrastructure software capabilities.
Therefore, Microsoft upgraded its Windows Defender package to detect irregular activity from PowerShell and WMI. Fine tuning Windows Defender enabled Microsoft to double the number of incidents that the firewall blocked in Q2 2017 compared to the previous quarter. That success against Misfox would also trap other viruses that exploit PowerShell.
Windows defense developments
Microsoft has created a whole range of commercial support products under the umbrella name Microsoft 365. This suite bundles in enhanced security measures alongside an updated version of Microsoft Office.As fileless malware almost exclusively attacks Windows, this is a Microsoft problem and the company’s response should rapidly reduce the threat of no-malware attacks.
How to stop fileless malware
The main defense against any type of malware is to keep your software up to date. As Microsoft has been very active in taking steps to block the exploitation of PowerShell and WMI, installing any updates from Microsoft should be a priority.Don’t kill JavaScript
Although JavaScript is a major channel for fileless malware, disabling it in browsers is not really a long-term solution to the malware problem. This is because most JavaScript appears in web pages for a reason. If you block it wholesale, you will find that many of the web pages you visit are either blank or missing elements. Another reason that filtering out JavaScript probably won’t help is that there is also a JavaScript interpreter embedded in Windows and that can be called from within a web page without the need for JavaScript.Other measures that you can take to block fileless malware intrusion are:
1. Set email policies
Caution employees about clicking on links in emails. Luring someone within the network to a website containing the malicious code is the easiest way to get fileless malware onto a Windows computer.Also, caution workers against opening attachments in emails not sent from trusted sources. Two types of documents are particularly hazardous:
- PDFs
- Microsoft Office documents
PDFs
Although the PDF format is widely used in business, it is also a great medium for spreading malware of all types. Fileless malware is aided by the ability to load PDFs in browsers immediately rather than downloading them. These PDFs can be delivered as email attachments or as “white papers” available from websites.If a PDF is downloaded before it is opened, your firewall has a chance to spot any malicious code within. Also, one of the problems of tracing a fileless attack is working out where it originated from. If the file is downloaded, it is available for analysis later. That is preferable to the disappearing malicious code that leaves no trace of its existence once the PDF viewing tab in the browser is closed.
Disable the ability of PDFs to load in browsers. You should also disable your PDF readers from activating JavaScript.
Microsoft Office macros
The use of Microsoft Office macros for spreading malware is well known in the cybersecurity community. Microsoft productivity software now ships with macro capabilities turned off. Employees who are sent email attachments in Word or Excel format may be tempted to turn macros on when prompted.A macro attack is not really a fileless malware conduit. However, the online availability of Microsoft products, including viewers for productivity documents for those who do not possess the Office suite, creates opportunities to run macros in the browser and launch calls to PowerShell or WMI.
Employee awareness
Explain to employees that they should never enable Microsoft Office macros in any document. Although macros are great for automating tasks, they have become such a potential hazard that it is better to find other methods to generate forms and documents. It is better that your workers do not become familiar with the possibility of running macros in documents.2. Disable Flash

Just like its Adobe stablemate, PDF, the web video delivery system Flash has become known as a malware-friendly feature in a web page. Most websites have already stripped out Flash and replaced it with HTML5 for video inclusion. Therefore, it is no great hardship to block this system from appearing in your browsers.
Browser actions
Microsoft Edge will not accept Flash code, so if that is your browser of choice, you don’t need to do anything. Both Firefox and Chrome give you the option to block Flash in their settings screens and Internet Explorer will not load Flash if you disable ActiveX.Read more here on why Flash is not secure.
3. Ban personal use of company resources
Introduce a policy that bans employees from using company computers to access personal email or leisure sites. This may be unpopular, but you can create a separate wifi network that allows employees to use personal devices so that they can access the internet during break periods.Industrial relations
Such services are popular with workers and they remove the temptation of staff to break the rules and try to access the internet through the main company network. The “own use” network can be kept completely separate from the main company system to reduce the risk of cross-infection. Setting up a separate wifi system and paying for another internet plan costs a lot less than the losses you could face from a malware attack.4. Protect your browsers
Create an office policy that only allows one browser type on company desktops. Then install browser protection on each computer. Microsoft produces Windows Defender Application Guard. This is part of Office 365 and it was written with specific procedures to protect against fileless malware attacks. This protection only covers Internet Explorer and Microsoft Edge.Windscribe
If you decide to use Firefox or Chrome as your office browser, then install the Windscribe extension on each browser. This utility will examine each web page that the browser loads and block any page that contains malicious code. The extension is mainly a VPN. However, as long as the extension is installed, the browser protection remains active even if the VPN is turned off. The extension also has an optional feature that will strip out social media “Like” buttons. These buttons are a security risk and they can also harbor code, which potentially could be a vector to load in PowerShell instructions.5. Strengthen user authentication
Microsoft suggests the spread of fileless malware is not caused by the existence of PowerShell, rather it is the result of weak user authentication on company networks and servers. A non-malware attack spreads throughout the network if installed on a computer whose user has high-level access rights to a large number of resources within the IT system. The Cobolt Kitty malware gained entry to the system by targeting the directors and infrastructure administrators of the victimized company. These superusers tend to have access to all parts of the network.Password protection
Employ password vaults and create different authentication points for each piece of equipment or service on the network. You should also consider implementing two-factor authentication that requires a code-generating physical gadget to provide a second layer of passkey that malware cannot emulate.Fileless malware issues
Fileless malware is a relatively recent method for hacker intrusion into a network. It is worrying because it is new and there are few people in the cybersecurity community with the knowledge and experience to deal with this problem. In fact, the mainstream anti-malware industry seems to have continued to overlook this methodology.Antimalware loophole
The entire operational system of antimalware programs is based on checking files. So, the move to a fileless system was a very clever move by hackers that has blindsided traditional antivirus procedures. Although antivirus producers have problems reimagining their strategies, Microsoft showed no hesitation at throwing resources at the problem and has contributed to a reduction of attack successes on Windows computers.Future developments
Right now, fileless malware only attacks the Windows operating system. However, hackers seem to have a standard pipeline of writing attacks for Windows first and then adapting those strategies for Mac OS and Linux later on. Android attacks usually come next and iOS gets hit last.The ability to deliver code through browsers should make fileless malware very easy to adapt to other operating systems. The only issue hackers face when porting this attack strategy is the need to discover an equivalent service on Linux and Macs that will match the usefulness of PowerShell. The fact that they haven’t found that facility yet is probably because they are so busy exploiting PowerShell right now.
System preparedness
The number one defense against fileless malware is to keep all of your software up to date. The second defense is to shut down browser security weakness, and the third action is to educate your employees about the websites they visit and the email attachments that they may encounter.Start now
The good news is that all of the main defense strategies against fileless malware cost nothing to implement. So, there should be nothing stopping you implementing a policy to tighten up your company’s defenses against fileless malware.from https://www.comparitech.com/blog/information-security/fileless-malware-attacks/
No comments:
Post a Comment