gilgamesh
Gilga Meshenger: Messaging in the Bluetooth Babylon!Some notes on the implementation, aka the glorious hack of Bluetooth Device Names. This application was original based on the Android SDK BluetoothChat sample. It used insecure (unpaired) and secure (paired) Bluetooth RFComm sockets to allow for short messages to be sent between devices. The primary modification that this project has made has been to add support for a "Broadcast" mode, that uses the Bluetooth device name, that is public visible during the Discovery process, as the message transport itself.
The design goals of this project are:
- A truly decentralised application that requires only Bluetooth connectivity and has no central user registry
- Incredible ease of use that ensures all "mesh" connectivity happens with as little user involvment as possible
- Ability to enable trust or reputation for specific users or devices you message with
- A very transient app that stores no data permanently
- Ability to share the app easily between devices
- A "fire and forget" mode, where the user can enter a message, put the phone in their pocket, and walk around and area and have it broadcast to all devices it encounters
Gilamesh also supports Linux: https://github.com/n8fr8/gilgamesh/blob/master/docs/gilgamesh.sh
The key innovations/hacks/revelations that led us to this point were:
- As of recent Android versions, you can call an API to set your the device's Bluetooth visibility to a very long time ~1 hour
- You can dynamically change the Bluetooth device name, and it can be long - up to 248 bytes encoded as UTF-8
- That the first two things above could be wrapped mostly in API calls the user did not have to see or worry about
- This app supports both a public broadcast mode, and a private, direct message mode. It is easy to use to both. The direct message mode is optionally secured and encrypted at the Bluetooth level if you have paired with the device/user you are connected with.
- Impersonation is combatted by simplified user id's to a short (6 character alphanumeric) value, based on the device's unique Bluetooth ID. This makes them speakable and easy to remember. If someone says "trust messages from A1BC99" then likely you will be able to rememember that.
- If you pair with a user (using standard Bluetooth pairing settings), their userid will be appended with a *, to make it even easier to know this is someone you should trust
- The app ONLY works in Bluetooth mode, so though is no confusion when it might be using 3G/4G, Wifi or some other mode, and possibly go through a centralised server
- The code is open-source, very small, and the entire app is only 28kb making it easy to audit, test and share
- We make it easy to "retweet" a message by long pressing on it, which enables reputation for something to be built up by multiple people resharing it. If the user has paired with the user, you will also see the * next to the name to further indicate trust.
------------------------
Gilgamesh: Twitter over Bluetooth
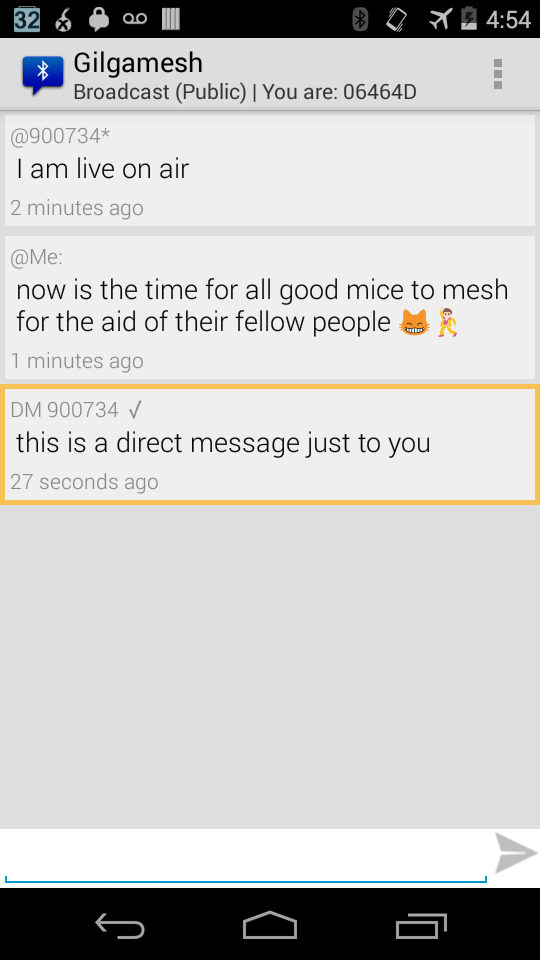
Hey, looks, it is like Twitter… except without any Internet! The Gilgamesh App continues to evolves, and is now tagged at 0.0.4. You can unofficially find it on FDroid thought it might take a bit for the latest code to show up there.
The primary update is that I have made the user interface look somewhat like a real app. This includes an easy popup menu to reshare (“retweet”) messages, which helps expand the reach of any message, while the human aspect of it combats spam and false information.
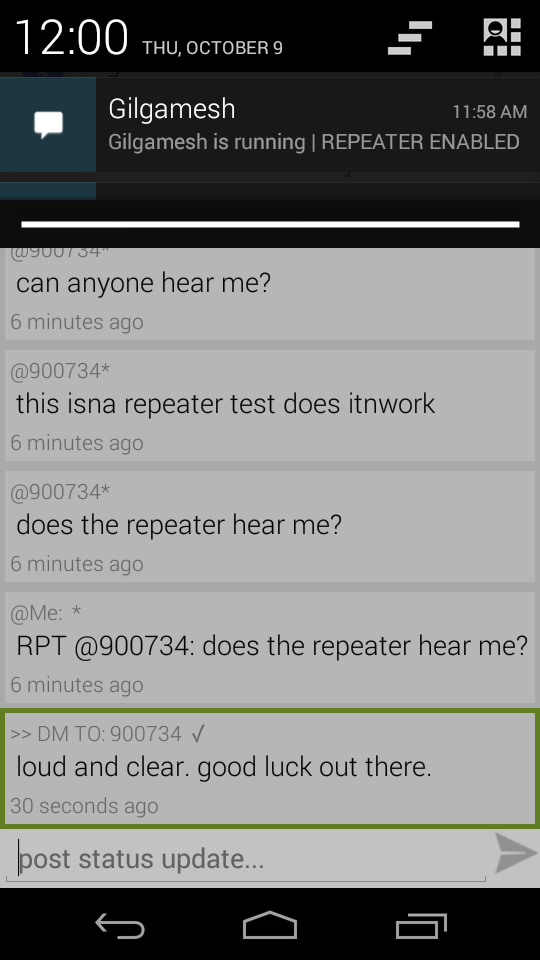
I have also added the ability to send a direct (private) message to anyone easily, as well. The direct messages will be queued and stored until delivered, which means you can send a message when someone is out of range, and it will be delivered if they happen to come into range. Delivery is indicated by a ✓mark.
This is all still operating using the plain text Bluetooth Discovery name hack that I’ve been writing about here for the last week, or so. Any Bluetooth device be it a $1000 iPhone or a $10 Nokia can participate in this network simply by changing their Bluetooth name to have a space in front of it, and then writing their own status updates there. They can view all of the messages as well, by scanning for nearby devices. This Android app simply builds on top of that network to support private messages, and a persistent log of all status/names encountered.
Finally, just to review some of the privacy-enhancing aspects of this app:
- If you just want to listen/consume information, you do not need to broadcast (make your device visible), making it very difficult to target your device
- The passive broadcast/discovery conduit allows for people that do not know each other, to passively and async exchange information in public spaces, with their devices out of sight (in their pockets)
- The asynchronous direct message features allows the exchange of messages in public places without any direct or visible interaction between parties
- All data received in the app is stored in memory, and not permanently stored to the device. This means killing the app wipes all memory clean, leaving no trace behind.
- All user identifiers are derived from the device’s ID, and though simple to remember, are not “friendly” in anyway that allows for easy social engineering impersonation attacks
- If Bluetooth pairing is done between devices, an extra level of identity verification is provided, and an * is tagged to all identifiers when displayed to ensure this is who you think it is.
- For Direct messages, any device which you have paired with, will use the Bluetooth “secure” socket connection mode, which provides a basic level of encryption and verification
- No registration, real name, phone number or email is required, providing no link to any other identity
- All resharing/re-broadcasting of information is powered by human minds and human hands, making it more difficult for any attacker to poison the information flow
from http://openideals.com/2014/10/06/gilgamesh-twitter-over-bluetooth/